Continuous Access Evaluation is a great improvement to Azure AD in terms of security. It greatly reduces the lag time between an administrator making a change, until that change is actually enforced for the user. Continuous Access Evaluation (CAE) has been in public preview for a while but was finally made generally available on January 10th 2022. Microsoft has enabled CAE for all tenants by default and it can only configured or disabled if the tenant has an Azure AD Premium 1 License or better.
Contents
- What is Continuous Access Evaluation
- How does Continuous Access Evaluation work?
- Requirements and Limitations
- Monitor Continuous Access Evaluation
- User Experience
What is Continuous Access Evaluation
When a user attempts to sign-in to Azure AD (or any application that uses Azure AD for authentication), the conditions of the sign-in are evaluated. Depending on policies the user is either granted or denied access. If the sign-in is successful the user is given an access token that is valid for one (1) hour. Once the access token expires the client is directed back to Azure AD, conditions are re-evaluated and the token is refreshed for another hour. This lag time of one hour means that an administrator can reset the users password or even disable the account, but the user will still have access until the token is refreshed. Many organizations have expressed concerns about this lag time because of the potential security issues associated with it.
Continuous Access Evaluation (CAE) attempts to solve some of these issues by giving applications such as SharePoint, Exchange, Teams etc. the ability do detect changes in the user session such as a location change. Since applications need to be CAE-capable, existing applications would need to implement CAE support before real-time changes to the sessions can be evaluated. Applications that do not support CAE will continue to use access tokens that are valid for 1 hour. Microsoft has stated that the goal is to provide instant enforcement but it might take a few extra minutes in the initial versions. The following services will be CAE-capable in the initial rollout: Exchange Online, Teams, SharePoint Online and Microsoft Graph. The list of known-events that CAE supports as of now are listed below:
- User Account is deleted or disabled
- Password for a user is changed or reset
- User changes location
- MFA is enabled for the user
- Admin explicitly revokes all Refresh Tokens for a user
- High user risk detected by Azure AD Identity Protection
- More will be added in the future
Below are two examples of two common scenarios with and without Continuous Access Evaluation:
| Without CAE | With CAE | |
| Session Revoked | – Enforced when access token is refreshed – Can take up to 1 hour | – Signal to revoke session is sent to all cloud applications. – Access blocked within minutes |
| Change Location | – Enforced when access token is refreshed – Can take up to 1 hour | – Cloud apps download and enforce policies locally – Instantly enforced |
How Does Continuous Access Evaluation Work?
Since applications like Exchange and Teams subscribe to events from Azure AD it is possible for Azure AD to inform the application that something has changed and ask the user to request a new access token. Likewise the applications can also notify Azure AD if something changes, for example if the user switches from a trusted to non-trusted network.
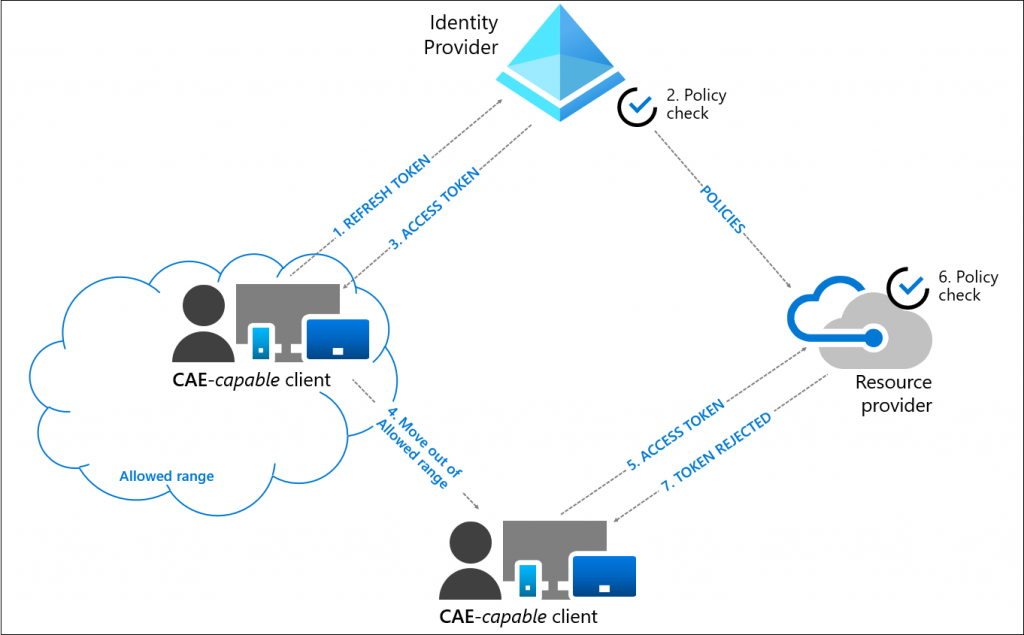
Here is a description of how Continuous Access Evaluation flow works:
- A user attempts to sign-in to a CAE-capable client (Teams client, Outlook etc.). The conditions of that login is evaluated and access is either granted or denied.
- On a successful login the user is given an access token and is allowed to access the resource.
- An administrator explicitly revokes the users session due to a security concern. An event will be sent to the resource provider (Teams, SharePoint, Exchange etc..) from Azure AD.
- The resource provider evaluates the validity of the access token.
- In this case, the resource provider denies access, and sends a claim challenge (re-authentication) back to the client.
- The CAE-capable client understands the claim challenge and the process is restarted from step 1, where the user is asked to reauthenticate and the conditions of the sign-in are re-evaluated.
Requirements and Limitations
Continuous Access Evaluation (CAE) does not require any licenses by itself, in-fact it is available in the free-tier of Azure AD. However since CAE is configured using Conditional Access, an Azure AD Premium 1 license is required to do any customization, such as only enabling CAE for specific users. Likewise if CAE is to be used with risk based events an Azure AD Premium 2 license is required.
Here are some of the possible limitations with Continuous Access Evaluation that could be relevant for your organization:
- Changes in Group Membership / Conditional Access policies can take longer to apply if used with CAE. The reason for this is that there is a delay in replication between Azure AD and the resource providers like Exchange and SharePoint, meaning changes could take up to 24 hours to apply. Microsoft has made optimizations to reduce the delay but this work is not completed yet.
As a workaround the Revoke Sessions button in Azure AD or the Revoke-AzureADUserAllRefreshToken PowerShell cmdlet can be used. Revoking the users refresh token would be considered a critical event and the CAE-capable client would trigger a re-authentication. If the client does not support CAE a regular 1 hour token will be provided. - Trusted MFA Locations and Country based Conditional Access Policies
Continuous Access Evaluation do not support location based conditions like MFA Trusted IP’s or country based locations defined in Conditional Access. In order for location based policies to be enforced in real-time by CAE, Microsoft recommends to only use the IP based Conditional Access condition.
Monitor Continuous Access Evaluation
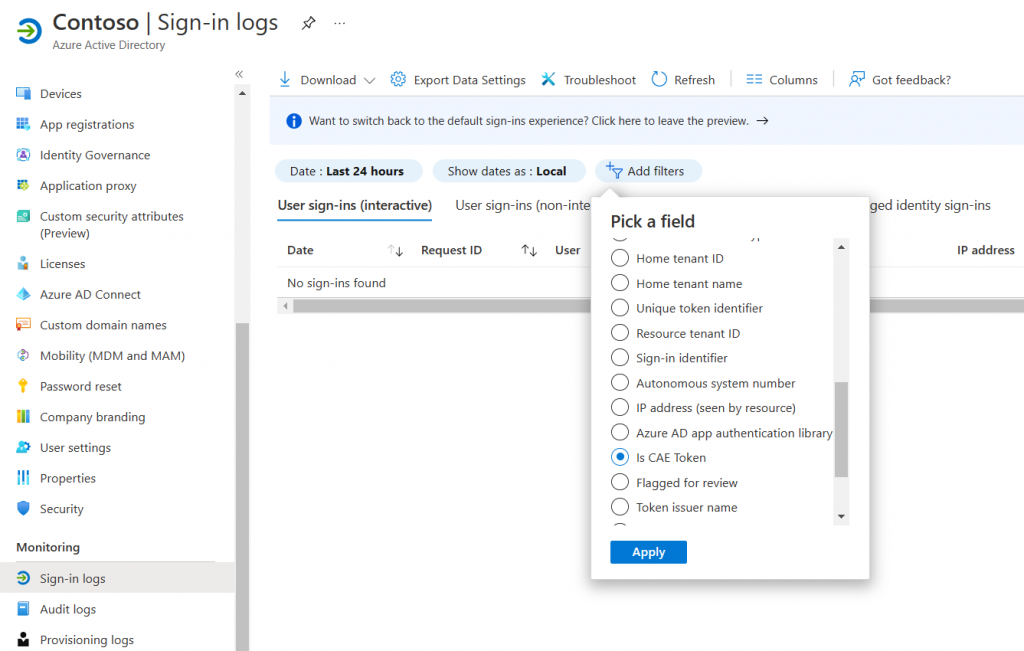
Microsoft has added a new filter to the Azure AD Sign-in logs that allows us to see if a session is using CAE or not. To view recent sign-ins with CAE apply the Is CAE Token filter.
- Open Azure Active Directory in the Azure Portal
- Select Sign-in Logs
- Click Add Filters and choose Is CAE Token
End-User Experience
In this example a user is signed into Outlook on the web (outlook.office.com). While the user is signed in an Administrator revokes the user’s session. Shortly after the session has been revoked by and administrator the user is taken back to the logon screen for re-authentication. During my testing it took somewhere between 2-5 minutes before the user was sent back to the sign-in screen, not perfect but this is a lot better than waiting an hour.