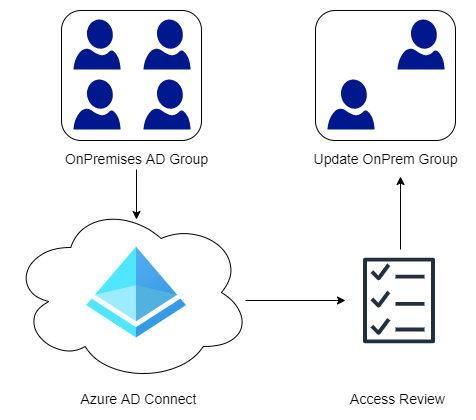
In some of my earlier post I have talked about Access Reviews that are part of the Identity Governance tools in Azure AD. One of the limitations is that on-premises groups cannot be edited directly from Azure AD, hence our Access Review cannot modify the group based after a review. In order to mitigate this we will use a PowerShell Module from Microsoft that will read the Access Review and then generate the commands needed to make the required changes in the on-premise environment. If you are not familiar with Access Packages and Access Reviews start by reading my post on Getting Started with Entitlement Management and Access Reviews: Manage Guest Users.
Contents
Prerequisites
First we need to create an App Registration in Azure AD that will be used by the PowerShell module to read our Access Review. This application will be used to authenticate to Azure AD and read our Access Review.
- In the Azure Portal head over to App Registration in Azure AD.
- Add a new Application and give it an appropriate name.
- Once the application has been created note the Application (client) ID.
- On the left-hand menu click API Permissions.
- Click Add Permission then choose Microsoft Graph.
- Next choose Application Permissions.
- Add the following permissions: AccessReview.ReadAll, Group.ReadAll and User.ReadAll.
- The default User.Read is not required here and can be removed if desired.
- Once the permissions have been added click the Grant Admin Consent button.
- On the left-hand menu click Certificates & Secrets.
- Under Client Secrets click New Client Secret.
- Give the secret a name and specify the expiration.
- Note down the Secret Value (will only be displayed once)
We should now have an App Registration with the corresponding Application ID.
Creating the Access Review
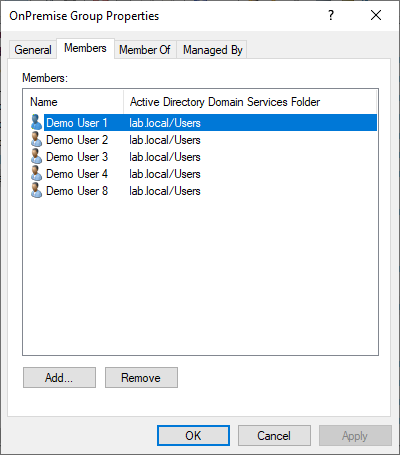
In this example the group is for simplicity sake called “OnPremise Group” and has 8 members. A more practical example could be the group that allows access to your VPN Service or access to some on-premise application. Make sure that the group you are testing with is within the synchronization scope of Azure AD Connect, else the group will not appear in Azure AD.
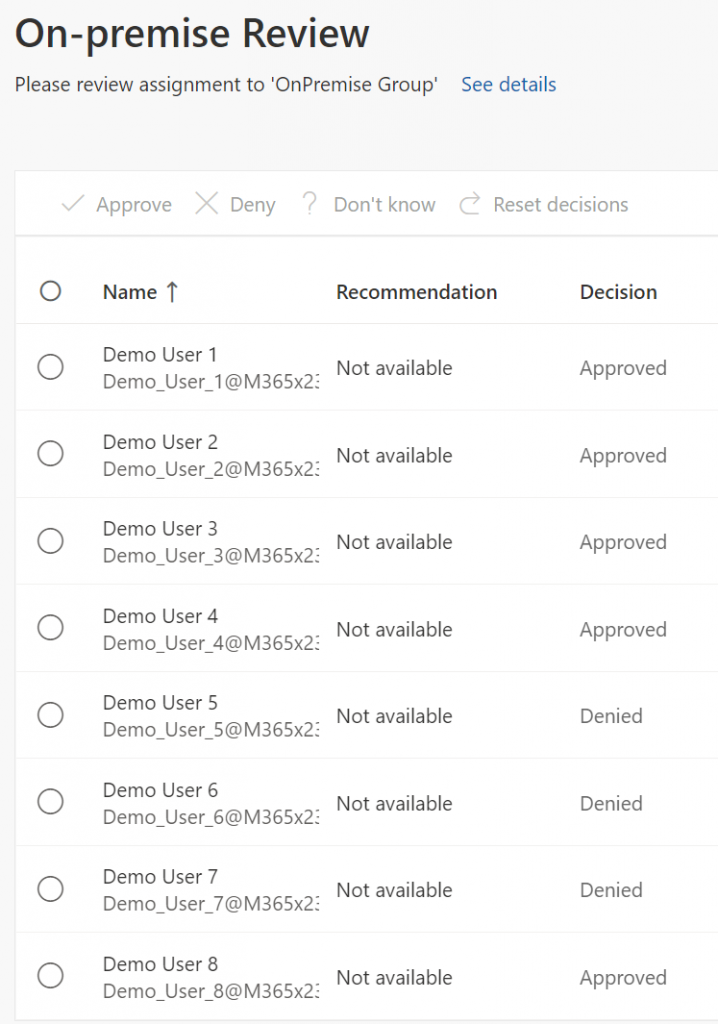
Next I created an normal access review that was targeted at the “OnPremise Group”. For demonstration purposes the Auto Apply Results To Resource option was disabled, though it wont make much of a difference since Azure AD cannot make modifications to an on-premise group anyway (this is the problem we are trying to solve). In the MyAccess Portal under Reviews, DemoUsers 5-7 were denied and the rest were approved.
Making On-Premises Changes
Now that our Access Review has been completed we can use the PowerShell Module from Microsoft to generate a script that will make the required changes in our on-premise Active Directory. The process below could of course be automated quite easily but that is beyond the scope of this post.
- Download and Import the PowerShell Module
- Connect to Azure AD and the Access Review using the Client Secret and Application ID that we collected earlier.
- Use the Get-AzureADARAllReviewsOnPrem command to retrieve the required changes for all Access Reviews. We wont use this in our example as we only want to focus on a single Access Review.
- Alternatively retrieve the changes required for a specific Access Review by specifying the reviewID or object ID displayed in the Azure AD Portal.
- Open the Text specified in step 3 or 4 then run those commands in the on-premises environment to make the required changes.
Important: Make sure that the file path and text file exists prior to running the commands.
Import-Module .\AzureADAccessReviewsOnPremises.psm1 Connect-AzureADMSARSample -ClientApplicationId xxxxxxxxxxx -ClientSecret xxxxxxxxxxx -TenantDomain xxxx.onmicrosoft.com Get-AzureADARAllReviewsOnPrem -filePath C:\Temp\OnPremCommands_AllReviews.txt Get-AzureADARSingleReviewOnPrem -reviewId xxxxxxxxxx -filePath C:\Temp\OnPremCommands_SingleReview.txt
Once the commands in the text file have been executed we can have a look in our “OnPremise Group” and the users that were Denied in the Access Review have now been successfully removed.