Azure AD’s B2B (Business to Business) functionality allows organizations to invite external users into their organization so that they can collaborate. However, very few of these organizations (in my experience) have any insight if these guest accounts are actually being used or not. There are several ways to manage guest users and one of them is using Access Reviews that is part of Identity Governance in Azure AD.
Contents
- What are Access Reviews?
- Requirements
- Creating An Access Review
- User Experience
- Limitations and Conclusion
What are Access Reviews?
Access Reviews allows administrators or those that have been defined as reviewers to review who has access to a specific set of resources such as a Team, SharePoint Site, Group, Azure Subscription, Application etc. Reviews can be scheduled at intervals or manually triggered to make sure only those individuals with a specific business justification have access to specific resources. For example, a person who previously worked in HR might retain their access to sensitive information after starting a new position that does not justify access to HR data. Using Access Reviews would uncover that the user still had access, and the reviewer could take the appropriate action. Even though the focus of this post is Guest User Access, Access Reviews could be used to asses a wide range of resources.
Requirements
Azure AD Identity Governance is included with the Azure AD Premium 2 license, that is included in bundles such as Microsoft 365 E5, Enterprise Mobility + Security E5 or as a standalone license. Note that Global Administrators do not need a license to configure the service, however there must be at least one Azure AD Premium 2 License in the tenant. By default there is a 1:5 ratio between Premium Licenses and Guest Users. So if you have 10 licensed users then you could have 50 guests. In environments that have a lot of guest users, switching from the default 1:5 ratio to MAU or Monthly Active Users based billing could drastically reduce costs. This is especially true since the first 50,000 MAUs per month are free for both Premium P1 and Premium P2 features. Check out Microsoft’s documentation here if you are curious on Monthly Active Users based billing.
Creating An Access Review
In this example we will be doing an Access Review on guest users in All Microsoft 365 Groups. The reason for choosing this is that there are a few minor limitations when the review scope is set to All Microsoft 365 Groups that you need to be aware of. I will be pointing out these limitations as we go though the access review. For the full feature set specify a single Group or Team.
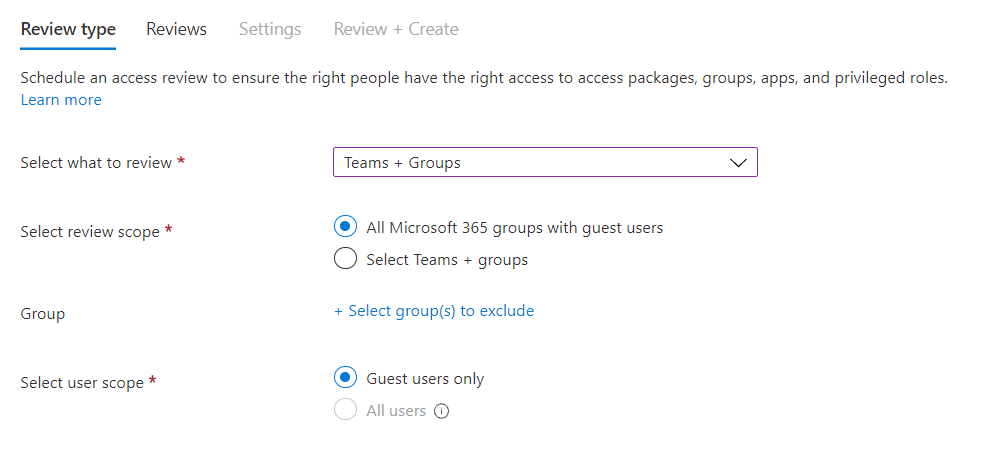
To create an Access Review navigate to the Identity Governance tab in Azure AD, then select Access Reviews. At the top choose to Create New Access Review. On the Review Type tab, select to review Teams + Groups and set the Review Scope to All Microsoft 365 Groups. Set the User Scope to Guest Users Only.
Note: Selecting multiple groups or applications results in the creation of multiple access reviews. For example, if you select five groups to review, the result is five separate access reviews.
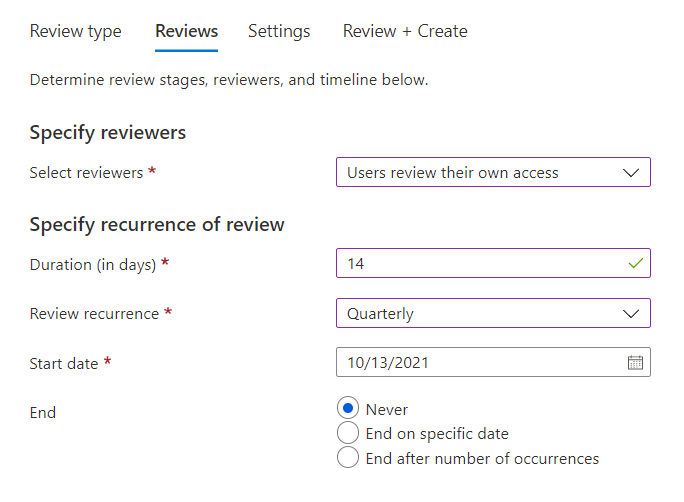
On the Reviews tab, we need to specify who should review the access for our guest users. The Select Reviewers dropdown gives us a couple of options, and we could have a manager or specific person in the company review all our guest users. However it is very unlikely that a single person has enough insight to make these decisions for the entire organization, so we will be asking our guest users to review their own access. This results in an email being sent to the guest user telling them to complete the Access Review.
Next we need to configure our Access Review Recurrence. The duration in days, this is the amount of days that users will have to complete the Access Review.
Limitation: When the Review Scope is set to All Microsoft 365 Groups it is impossible to set the review reoccurrence to one time only.
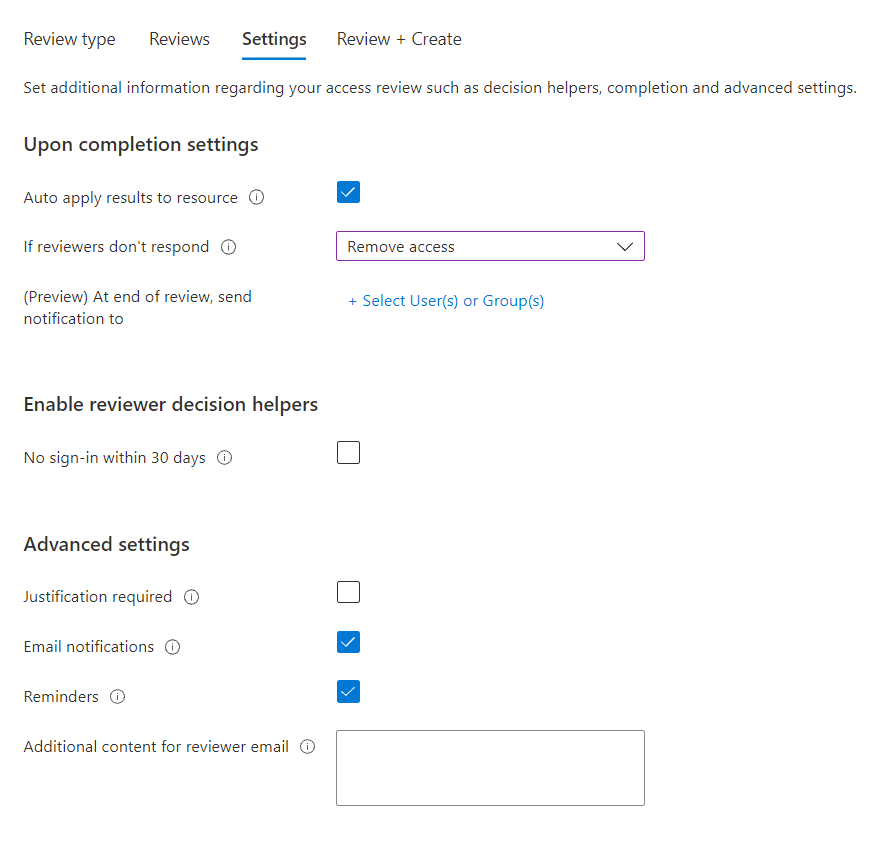
On the Settings tab, we can choose what happens when the Access Review is complete. The Auto Apply Results checkbox will automatically remove access at the end of the Access Review. If this checkbox is not enabled then you will need to remove access manually. Additionally we need to specify the action to be take if our guest users do not respond within the duration of the Access Review. Since we do not want stale guest users to have access to our data, we will remove their access if they do not respond.
The Reviewer Decision Helpers will let the reviewers know if the user has signed-in the last 30 days or not. Note that this does not mean that the user has used a specific resource, it simply means that the user has signed into Azure AD the last 30 days. The only exception to this is Azure AD Applications. If the access review is scoped against one or more applications the recommendations will reflect sign-in to that application. Since the guest user will be reviewing their own access, there is no need to enable decision helpers as user will know if they have logged into our organization or not the past 30 days.
Limitation: When the Review Scope is set to All Microsoft 365 Groups or the review scope contains more than only guest users, the choice to block and delete denied users from the tenant after 30 days is not present.
Under Advanced Settings we could require our reviewers (guest-users) to specify a justification as to why they need access to our organization. Disabling Email Notifications will require each user to go to the My Access Portal and review their access there so we will keep email notifications enabled. If Reminders are enabled Azure AD will send an email at the midpoint of the Access Review. In our example the review was set for 14 days and in this case the user would receive a reminder after 7 days.
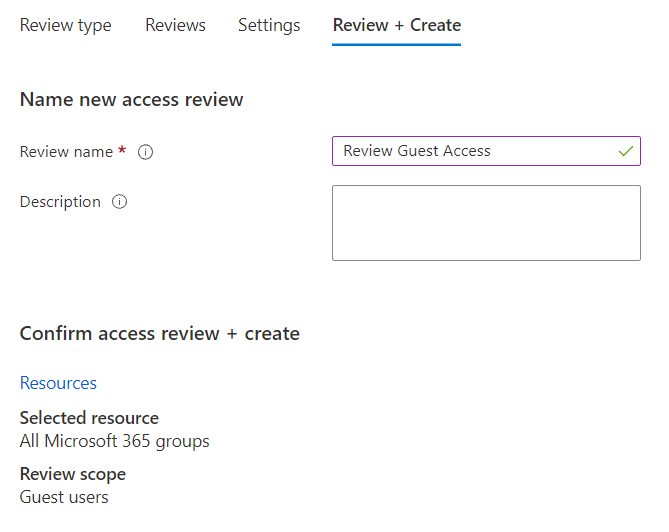
Finally on the Review + Create tab, give the Access Review a name and optionally a description.
User Experience
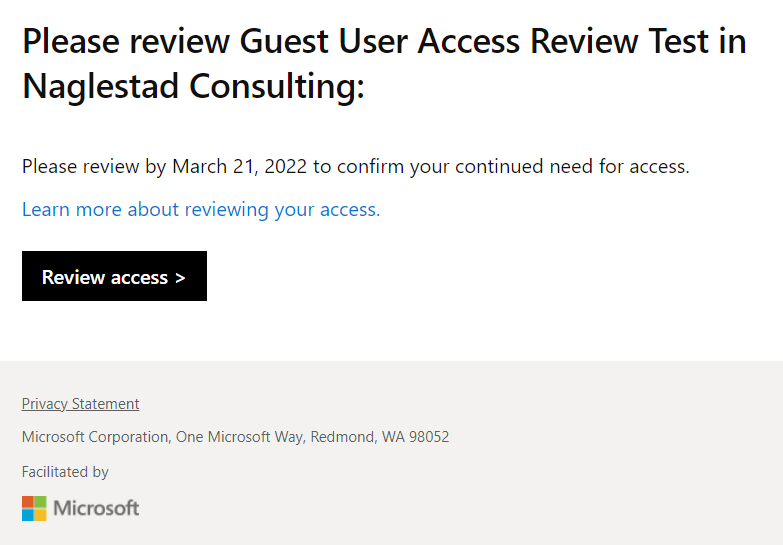
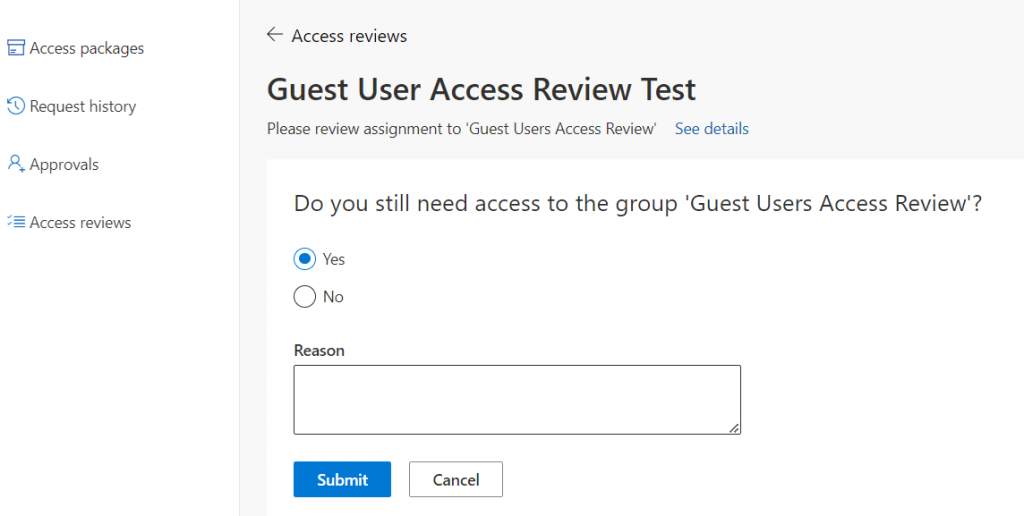
Users will now receive an email (if turned on) that will take them to the Identity Governance Portal (https://myaccess.microsoft.com) where they can complete the Access Review. Once the Access Review is complete
Limitations and Conclusion
All in all Access Reviews is a great tool and I would recommend taking advantage of them and the rest of the tools in Azure AD Identity Governance to any organization. The biggest limitation in my opinion is the option to block and remove the guest user automatically after 30 days is not present when the review type is set to All Microsoft 365 Groups, however it does work for single groups. This is a shame, because there is no other way to scope All Guest users except to add each group that contains guest users into our access review. A simple workaround is to create a new group, add all guest users to that group using PowerShell and then scoping an Access Review to that single group.
What about On-premises and Dynamic Groups? Well Dynamic Groups are useless from an Access Review point because they are based on specific rules/queries, hence Access Reviews cannot modify the group membership. The same problem exists for groups that have been synchronized with Azure AD Connect (membership is controlled on-premise). However there is a PowerShell module that can read the results of an Access Review and apply the required changes to on-premises groups, check out the module here. This would bypass the ownership issue and allow for the same flexibility as an Azure AD Group. I will cover this PowerShell module in a future post.