Many organizations leveraging Microsoft 365 and Azure, are utilizing hybrid identities with Microsoft’s Azure AD Connect synchronization tool. A nice feature that is not enabled by default is the ability to tick the “User must change password at next logon” attribute in your on-premise Active Directory and forcing users to update their passwords through Azure Active Directory.
If this is enabled in your directory or you are considering it, remember to enable Password Writeback in your Azure AD Connect configuration. This allows Azure AD to write the new password back to your on-premise Active Directory. It is also a good idea to enable Self Service Password Reset (SSPR), which allows users to reset or unlock their accounts from any web browser without having to contact Helpdesk.
On the AD Connect Server, open PowerShell and issue the command Get-ADSyncAADCompanyFeature to check if the ForcePasswordChangeOnLogOn has been set.
Get-ADSyncAADCompanyFeature PasswordHashSync : True ForcePasswordChangeOnLogOn : False UserWriteback : False DeviceWriteback : True UnifiedGroupWriteback : False
If the ForcePasswordChangeOnLogOn flag is set to false, then issue the following command to enable the feature.
Set-ADSyncAADCompanyFeature -ForcePasswordChangeOnLogOn $true
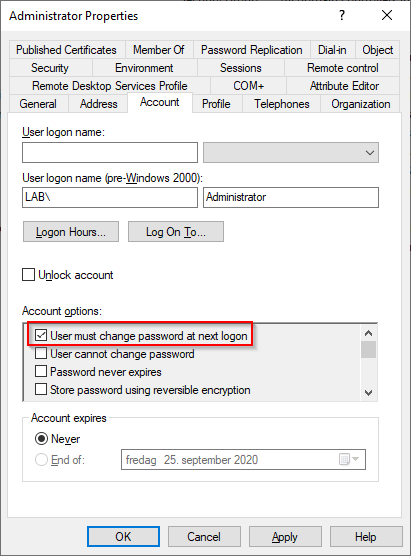
In the on-premise Active Directory locate a user that should have his/her password changed (the user must be part of the synchronization scope in Azure AD Connect) by checking the “User must change password at next logon” box.
Wait for Azure AD Connect to synchronize the changes to Azure AD (this can take a while). To verify that the attribute has been set in Azure AD issue the following PowerShell command and verify that the ForceChangePasswordNextLogin is set to true.
Get-AzureADUser -ObjectID username@domain.com | Select PasswordPolicies, PasswordProfile | fl
PasswordPolicies : DisablePasswordExpiration
PasswordProfile : class PasswordProfile {
Password:
ForceChangePasswordNextLogin: True
EnforceChangePasswordPolicy: False
}
Once we have verified that the attribute has been set in Azure AD, the user should be prompted to change their password on next login. Use an InPrivate/Incognito Window in your browser and point to for example portal.office.com.
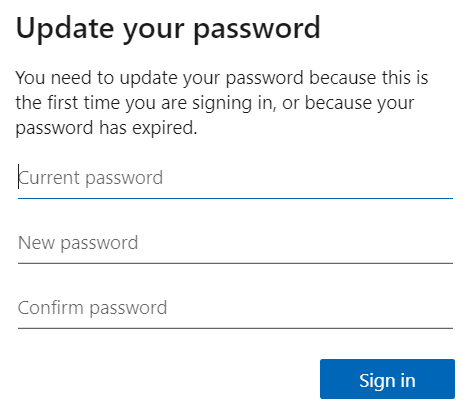
Once the password has been changed, it takes a few minutes before the new password will work. During my limited testing, the average was around 5 minutes before the user could access their account again.