Microsoft announced the deprecation of Legacy Authentication for Exchange Online back in 2019, unfortunately many organizations are still dependent on legacy based protocols. The deadline for enabling Modern Authentication for Exchange Online was initially in 2020, but Microsoft extended the deadline until H2 of 2021 due to the Covid-19 pandemic. In this post we will discuss the benefits of using Modern Authentication, how to enable it for Exchange Online and how to block legacy/basic authentication using Conditional Access.
Contents
- Legacy vs Modern Authentication
- Checking for Legacy Authentications
- Enable Modern Authentication in Exchange Online
- Blocking Legacy Authentication
Legacy vs Modern Authentication
So what exactly does Microsoft mean when they say Legacy Authentication? Well the short answer is any protocol that does not support MFA (Multi-Factor Authentication). Microsoft has created a list of protocols that they define as legacy protocols.
So why is this so important? Well according to Microsoft, enabling MFA increases security by 99%. Hence using older protocols that do not support MFA becomes a clear security risk. Many organizations are focused on having password policies that include long and complex passwords that users must change often. However we are all human. Humans tend to reuse the same password over and over, both for work, social media and other private accounts. If any of those had a security breach and passwords where compromised, all your accounts would be at risk. The conclusion becomes obvious: focus on areas that can increase security like Multi-Factor Authentication, FIDO2 and Passwordless security options, not password policies.
Have a look at this post from Alex Weinert the Director of Identity Security at Microsoft and Microsoft’s updated Password Guidance.
Checking for Legacy Authentications
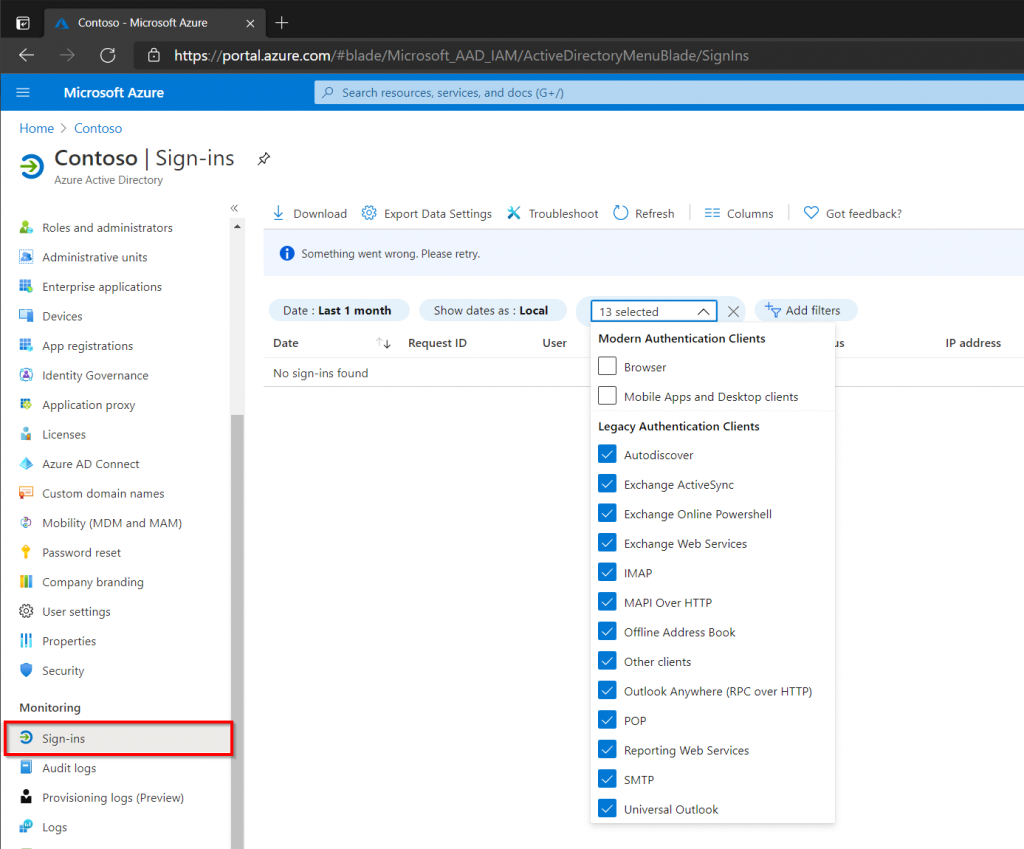
The simplest method to check if there have been any legacy based authentications the last month is to check the Azure AD sign-in logs.
- Open Azure Active Directory in the Azure Portal.
- Select Sign-ins under Monitoring.
- Add the Client App Filter.
- Select all the authentications methods under Legacy Authentication.
- Review the sign-ins and optionally export them in CSV or JSON.
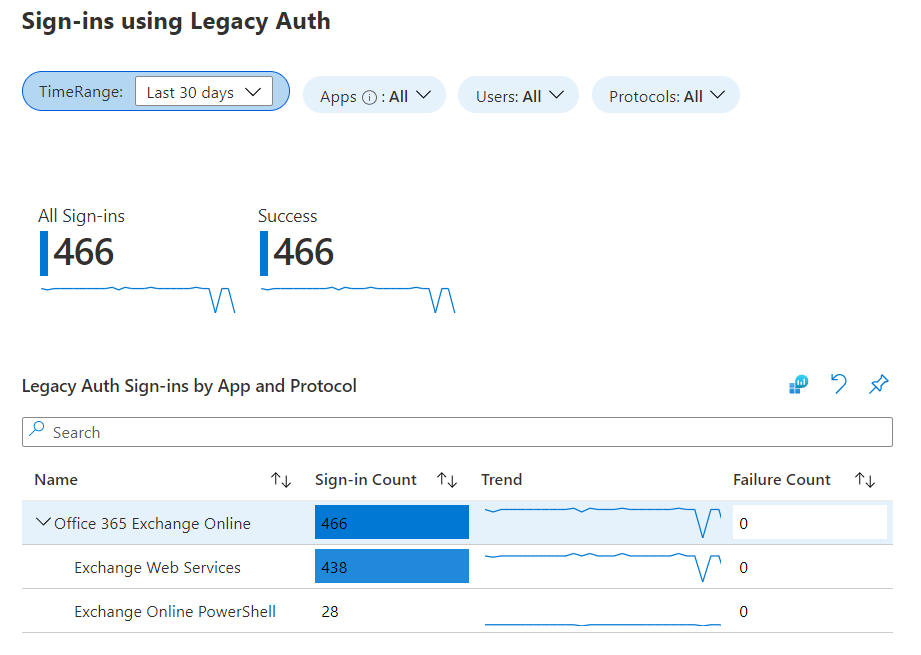
The Azure AD logs are great for recent events (last month), but what about historical data? Azure Log Analytics is a great tool for storing and querying large amounts of data from Azure AD. Since sign-in and audit logs can be forwarded directly into Azure Log Analytics, we can use a Log Analytics Workspace to get insights and a much more complete picture of our organization. If a Log Analytics Workspace has already been setup, click Workbooks (just below Sign-ins) and select the Sign-ins using Legacy Authentication report. This allows a much more visual insight into our data with simple filtering. See Microsoft’s documentation on how to create a Log Analytics Workspace.
Enable Modern Authentication in Exchange Online
Modern Authentication for Exchange Online is simple to activate through the Microsoft 365 Admin Center or through PowerShell. Any Azure tenant that was created before August 1st 2017 has Modern Authentication set to disabled by default. However newer tenants will have Modern Authentication enabled by default.
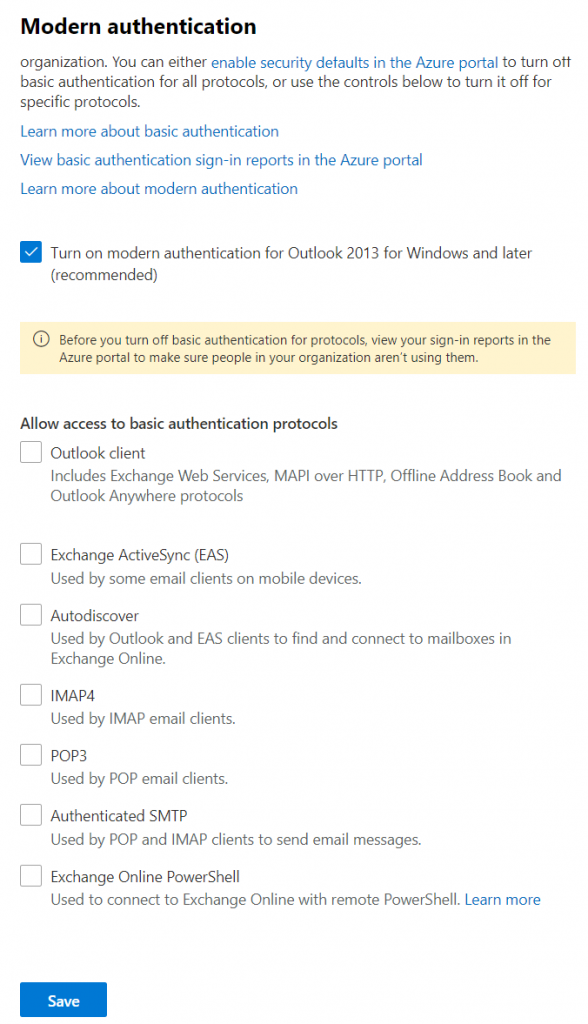
In the Modern Authentication window, make sure that the checkbox for Modern Authentication is enabled. Next you have the possibility of disabling Legacy Authentication for Exchange completely. However before doing so ask your self the following questions:
- What systems / users are using legacy authentication?
- Can all of these utilize modern authentication?
- Do I need to replace or upgrade any system to support modern authentication?
- Are there any services users depending on legacy authentication?
In just about every organization there is one or more system that does not support modern authentication. Instead of disabling the functionality completely, use Conditional Access to block legacy authentication. Then exclude those users / services that still depend on legacy authentication.
If PowerShell is preferred, use the commands below to enable Modern Authentication for Exchange Online.
Install-Module ExchangeOnlineManagement -Verbose Import-Module ExchangeOnlineManagement Connect-ExchangeOnline -UserPrincipalName admin@example.com -ShowProgress $true Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
Verify the change by running the following command
Get-OrganizationConfig | Format-Table Name,OAuth* -Auto
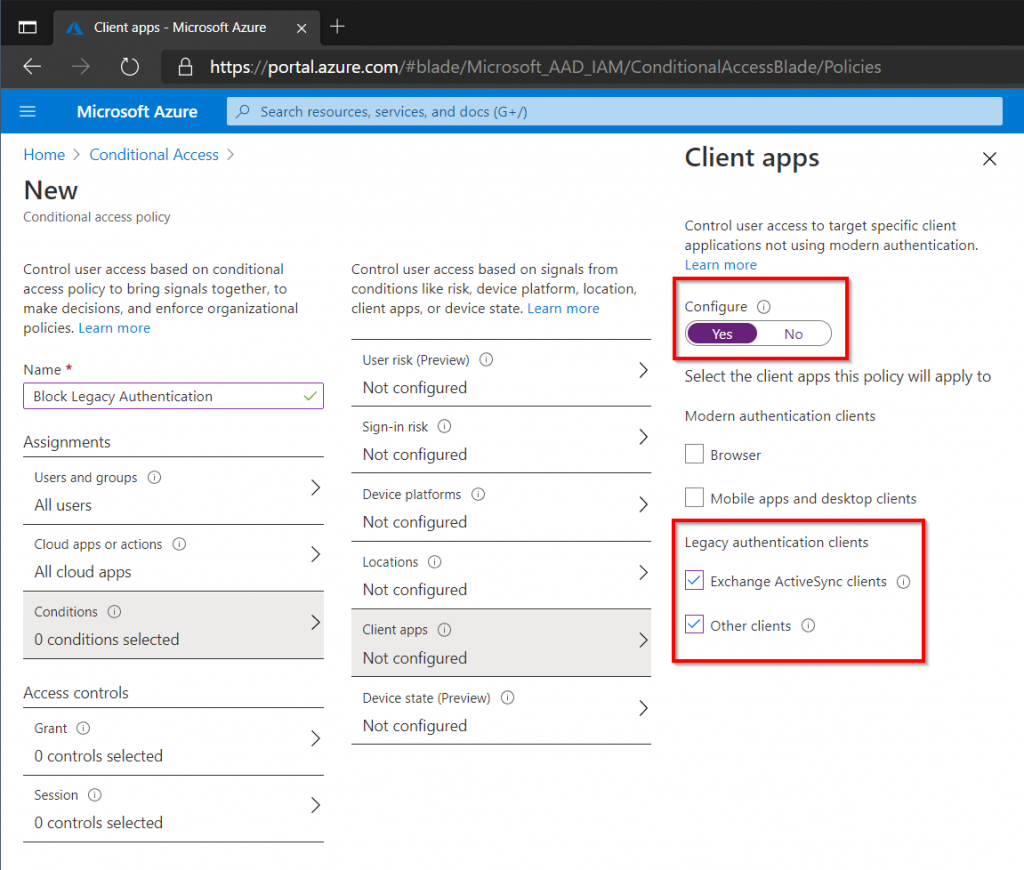
Blocking Legacy Authentication
Conditional Access allows organizations to test their readiness before Microsoft disables legacy authentication completely in Exchange Online. My post on Getting Started with Conditional Access, contains step-by-step instructions on how to block legacy authentication and other good practices.