Several customers recently made changes to their AD Connect setups, more specifically changes to what OU’s that are being synched synchronized. As we all know, when a user is removed from the synchronization scope the user is also deleted from Azure AD. However if there is a large amount of objects that need to be removed, AD Connect will show a stopped-deletion-threshold-exceeded error. This error occurs because the default deletion threshold is set to 500 objects. The threshold is designed to prevent mass-deletions accidentally. When the threshold is reached Azure AD sends an email notification to administrators informing them there has been an attempt delete a large number of objects.
If this error is encountered the first step is obviously to check if the deletions is intended or not. In my case the deletion was intentional as we were removing a specific OU that contained hundreds of users.
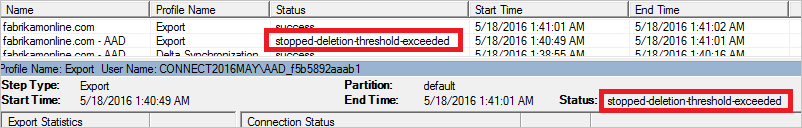
Start by checking the deletion threshold on the AD Connect Server. As mentioned above the default is 500.
Get-ADSyncExportDeletionThreshold
Next temporarily disable the deletion threshold by entering the following command. Provide Global Administrator credentials when prompted.
Disable-ADSyncExportDeletionThreshold
Now that the deletion threshold has been disabled, we can trigger a full synchronization. Alternatively wait for AD Connect to trigger a sync on its own.
Start-ADSyncSyncCycle -PolicyType Initial
Monitor the progress with the Synchronization Service (can be started from the start menu). Once all the desired deletions have been completed and no stopped-deletion-threshold-exceeded errors occur. The accidental deletion threshold can be re-enabled. The enable command will prompt for Global Administrator credentials just like the disable command did.
Enable-ADSyncExportDeletionThreshold -DeletionThreshold 500
For more information have a look at Microsoft’s documentation.


