A colleague made me aware of a new preview feature in Intune called Device Diagnostics. The feature lets you collect troubleshooting information from an online client without having to disturb the user. The feature collects a wide range of information on the users system and stores this data in the cloud for up to 28 days. The complete list of items collected is listed below. This is a really nice gem that support and operational departments should utilize fully!
Requirements
- Windows 10 version 1909 or later
- Devices must be corporate owned and enrolled into Intune
- Devices must be online
- Permissions (Global Admin, Intune Admin or a custom role with the Collect Diagnostic permission)
To check if the feature is enabled in your tenant open the Endpoint Manager Admin Center, and under Tenant Administration there should be an option for Device Diagnostics.
Data Collection
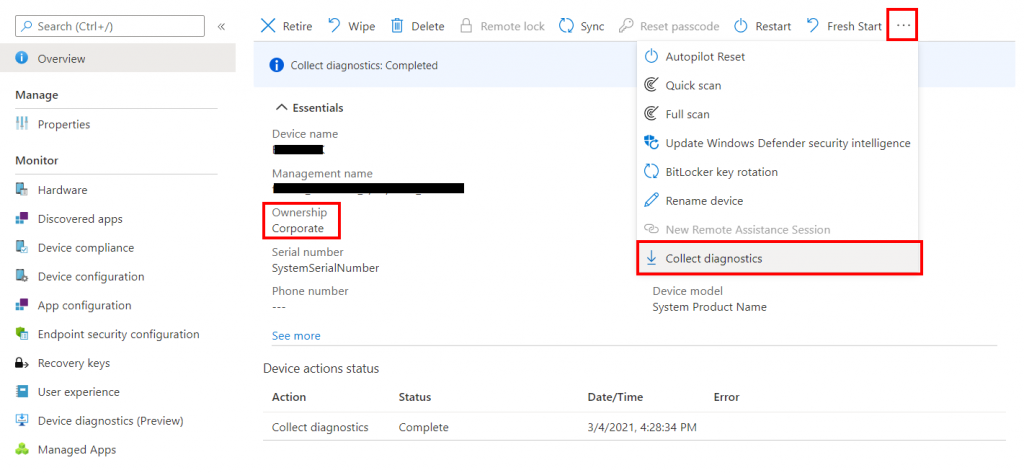
To collect diagnostic information from a device: firstly check that the device is corporate owned, then select the three dots to expand the top menu and select Collect Diagnostics. The data collection will take a few minutes.
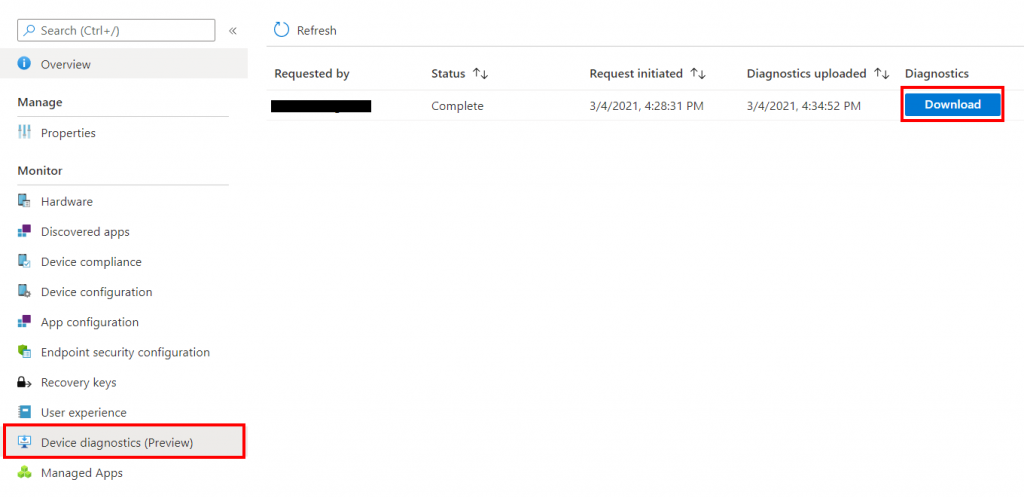
To view the current status and download the collected information select Device Diagnostic under Monitor. It is possible to have up to 10 diagnostic packages per device.
Review Collected Data
Within the diagnostics zip file there are 50 folders, one for each element in the collection list. At the very bottom there is an XML file called results.xml that will contain information on the commands that where executed and if they were successful or not (see the picture below). If a command fails the resulting folder in the diagnostic file will be empty.
Unfortunately the filenames within the diagnostic file only contain words like export, output or events, providing no details as to what the file actually contains. If you wanted to view the list of programs installed on the device, folders 6 and 10 would have to be reviewed. Whereas Windows Updates are located in folder 50.
Use the following script from Microsoft to parse the extracted folders into something more readable.
Usage: Devicediagnostics.ps1 MyDeviceDiagFile.zip
param($DiagnosticArchiveZipPath)
#region Formatting Choices
$flatFileNameTemplate = '({0:D2}) {1} {2}'
$maxLengthForInputTextPassedToOutput = 80
#endregion
#region Create Output Folders and Expand Zip
$diagnosticArchiveTempUnzippedPath = $DiagnosticArchiveZipPath + "_expanded"
if(-not (Test-Path $diagnosticArchiveTempUnzippedPath)){mkdir $diagnosticArchiveTempUnzippedPath}
$reformattedArchivePath = $DiagnosticArchiveZipPath + "_formatted"
if(-not (Test-Path $reformattedArchivePath)){mkdir $reformattedArchivePath}
Expand-Archive -Path $DiagnosticArchiveZipPath -DestinationPath $diagnosticArchiveTempUnzippedPath
#endregion
#region Discover and Move/rename Files
$resultElements = ([xml](Get-Content -Path (Join-Path -Path $diagnosticArchiveTempUnzippedPath -ChildPath "results.xml"))).Collection.ChildNodes | Foreach-Object{ $_ }
$n = 1
# only process supported directives
$supportedDirectives = @('Command', 'Events', 'FoldersFiles', 'RegistryKey')
foreach( $element in $resultElements) {
# only process supported directives, skip unsupported ones
if(!$supportedDirectives.Contains($element.Name)) { continue }
$directiveNumber = $n
$n++
$directiveType = $element.Name
$directiveStatus = [int]$element.Attributes.ItemOf('HRESULT').psbase.Value
$directiveUserInputRaw = $element.InnerText
# trim the path to only include the actual command - not the full path
if ($element.Name -eq 'Command') {
$lastIndexOfSlash = $directiveUserInputRaw.LastIndexOf('\');
$directiveUserInputRaw = $directiveUserInputRaw.substring($lastIndexOfSlash+1);
}
$directiveUserInputFileNameCompatible = $directiveUserInputRaw -replace '[\\|/\[\]<>\:"\?\*%\.\s]','_'
$directiveUserInputTrimmed = $directiveUserInputFileNameCompatible.substring(0, [System.Math]::Min($maxLengthForInputTextPassedToOutput, $directiveUserInputFileNameCompatible.Length))
$directiveSummaryString = $flatFileNameTemplate -f $directiveNumber,$directiveType,$directiveUserInputTrimmed
$directiveOutputFolder = Join-Path -Path $diagnosticArchiveTempUnzippedPath -ChildPath $directiveNumber
$directiveOutputFiles = Get-ChildItem -Path $directiveOutputFolder -File
foreach( $file in $directiveOutputFiles) {
$leafSummaryString = $directiveSummaryString,$file.Name -join ' '
Copy-Item $file.FullName -Destination (Join-Path -Path $reformattedArchivePath -ChildPath $leafSummaryString)
}
}
#endregion
Remove-Item -Path $diagnosticArchiveTempUnzippedPath -Force -Recurse
List of Information Collected
At the time of writing the following information is collected:
Registry Keys:
- HKLM\Software\Microsoft\IntuneManagementExtension
- HKLM\SOFTWARE\Microsoft\SystemCertificates\AuthRoot
- HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall
- HKLM\Software\Policies
- HKLM\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL
- HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection
- HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall
- HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
Commands:
- %programfiles%\windows defender\mpcmdrun.exe -GetFiles
- %windir%\system32\certutil.exe -store
- %windir%\system32\certutil.exe -store -user my
- %windir%\system32\Dsregcmd.exe /status
- %windir%\system32\ipconfig.exe /all
- %windir%\system32\mdmdiagnosticstool.exe
- %windir%\system32\msinfo32.exe /report %temp%\MDMDiagnostics\msinfo32.log
- %windir%\system32\netsh.exe advfirewall show allprofiles
- %windir%\system32\netsh.exe advfirewall show global
- %windir%\system32\netsh.exe lan show profiles
- %windir%\system32\netsh.exe winhttp show proxy
- %windir%\system32\netsh.exe wlan show profiles
- %windir%\system32\netsh.exe wlan show wlanreport
- %windir%\system32\ping.exe -n 50 localhost
- %windir%\system32\powercfg.exe /batteryreport /output %temp%\MDMDiagnostics\battery-report.html
- %windir%\system32\powercfg.exe /energy /output %temp%\MDMDiagnostics\energy-report.html
Event Viewers:
- Application
- Microsoft-Windows-AppLocker/EXE and DLL
- Microsoft-Windows-AppLocker/MSI and Script
- Microsoft-Windows-AppLocker/Packaged app-Deployment
- Microsoft-Windows-AppLocker/Packaged app-Execution
- Microsoft-Windows-Bitlocker/Bitlocker Management
- Microsoft-Windows-SENSE/Operational
- Microsoft-Windows-SenseIR/Operational
- Setup
- System
Files:
- %ProgramData%\Microsoft\DiagnosticLogCSP\Collectors*.etl
- %ProgramData%\Microsoft\IntuneManagementExtension\Logs*.*
- %ProgramData%\Microsoft\Windows Defender\Support\MpSupportFiles.cab
- %ProgramData%\Microsoft\Windows\WlanReport\wlan-report-latest.html
- %temp%\MDMDiagnostics\battery-report.html
- %temp%\MDMDiagnostics\energy-report.html
- %temp%\MDMDiagnostics\mdmlogs-<Date/Time>.cab
- %temp%\MDMDiagnostics\msinfo32.log
- %windir%\ccm\logs*.log
- %windir%\ccmsetup\logs*.log
- %windir%\logs\CBS\cbs.log
- %windir%\logs\measuredboot*.*
- %windir%\Logs\WindowsUpdate*.etl
Known Issues
- Unzipping diagnostics with 7Zip returns empty folders – This is a known issue with compressed files created by Windows and 7Zip. We recommend using a different tool to unzip the files.
- If uploading diagnostics to Intune takes more than 30 seconds, the diagnostic collection task will fail – This is a known issue with the DiagnosticLog CSP that has been fixed in KB4601315 and KB4601319, which were released on February 2th, 2021 via Windows Update. Please ensure your machines have been updated.
- Device diagnostics has been pending for a while, what should I do? – Best practice is to ensure the device can communicate with the service. Forcing a device check-in will ensure the device is able to reach the Intune service. If the device can reach the service, retry the diagnosticsaction.
- How long are the diagnostics available? – Diagnostics are available for download for 28 days and then automatically deleted per data retention requirements.
- How many diagnostics can I run on a device? – Each device may have up to 10 diagnostics. After 10, the oldest set of diagnostics is removed and replaced.
- What’s the maximum size of diagnostics I can collect? – 250mb of compressed files currently.


