Many people have already discovered the Microsoft Authenticator App and are using it to approve or deny multi-factor authentication requests. However the Microsoft Authenticator App can also be used for Passwordless Authentication which increases security and provides a better sign-in experience for end-users. Passwordless Authentication with the Microsoft Authenticator app is just one way of reducing our dependency on passwords. Read my blog post on Getting Started with Passwordless Authentication for an introduction to passwordless methods and why all organizations should have this on their roadmap for the future.
Contents
- Requirements
- Enable Combined Security Information Registration
- Enable Microsoft Authenticator Authentication Method
- Device Registration
- Sign-in Using Passwordless Authentication
Requirements
- Azure AD Multi-Factor Authentication enabled and configured.
- Push Notifications must be enabled as a verification method.
- Combined Registration Experience must be enabled.
- Latest version of Microsoft Authenticator app.
- IOS or Android device registered in Azure AD.
Enable Combined Security Information Registration
The first step is to make sure that Combined Security Information Registration is enabled in the tenant. By enabling this feature users do not have to register their security information multiple times for multiple services. For example the security information that a user provides for Multi-Factor Authentication (MFA) can be automatically used for Self-Service Password Reset (SSPR).
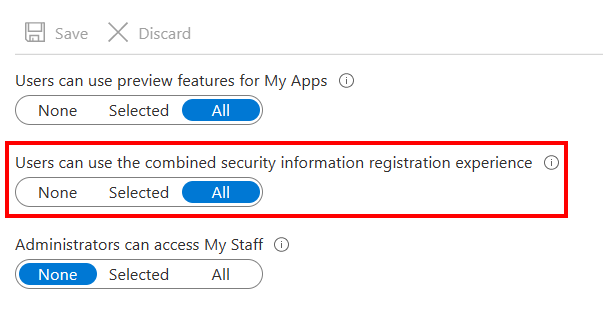
- From the Azure AD blade select User Settings.
- At the bottom select Manage User Feature Settings.
- Make sure that the Users can use the combined security information registration experience is set to All as in the picture below.
Now that the Combined Security Information Registration feature is enabled we can enable FIDO2 Security Keys as an Authentication Method in Azure AD.
Enable Microsoft Authenticator Authentication Method
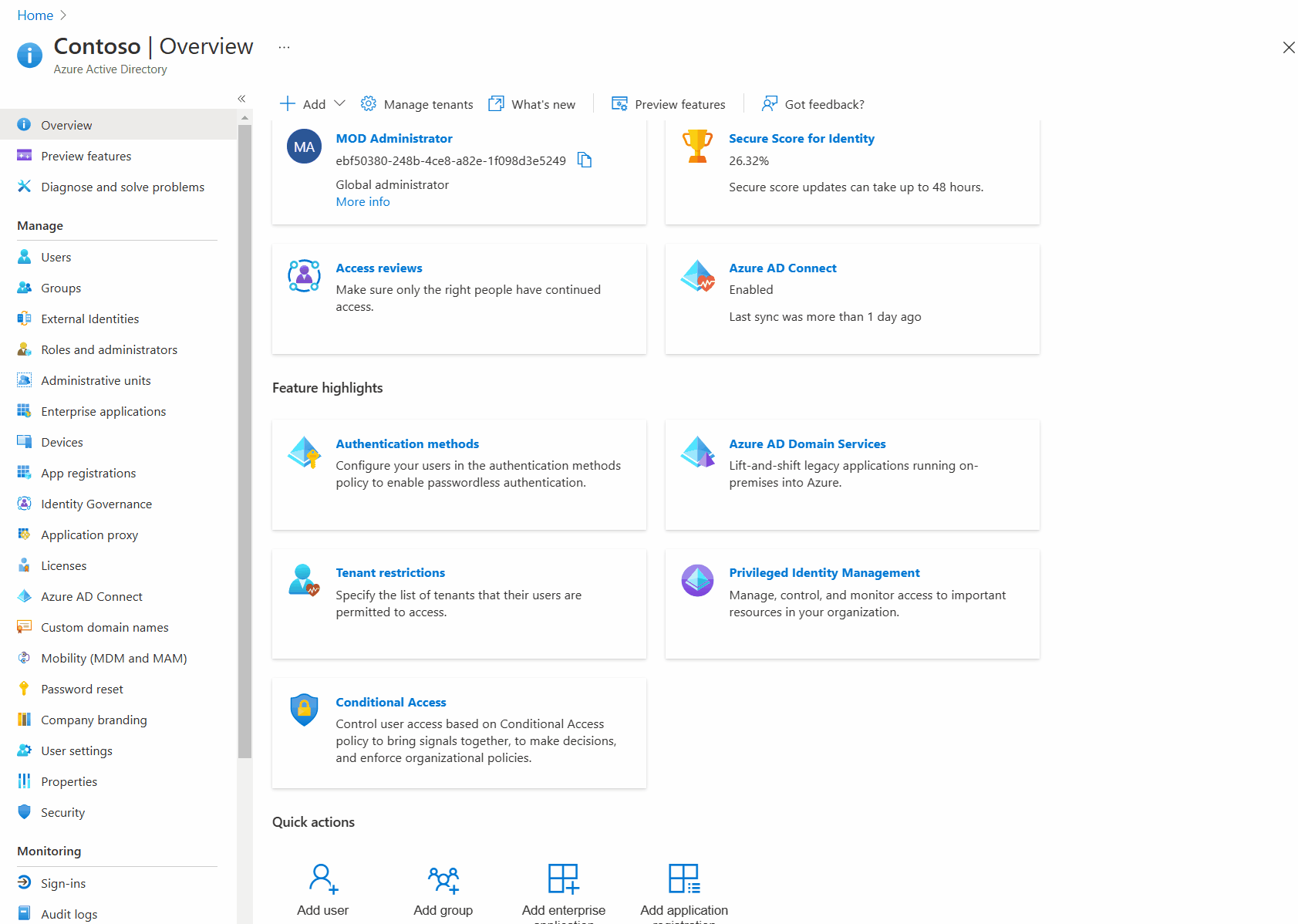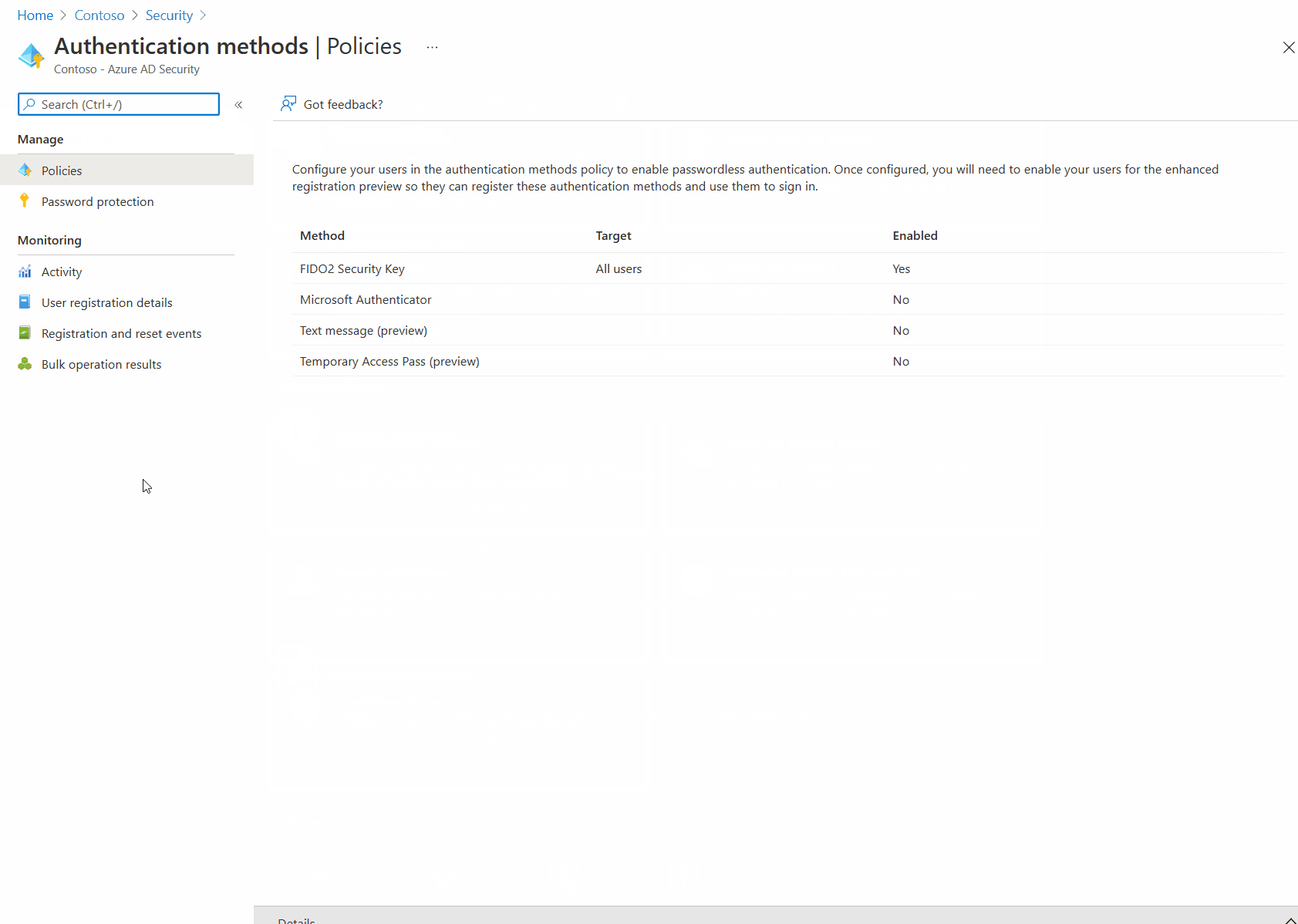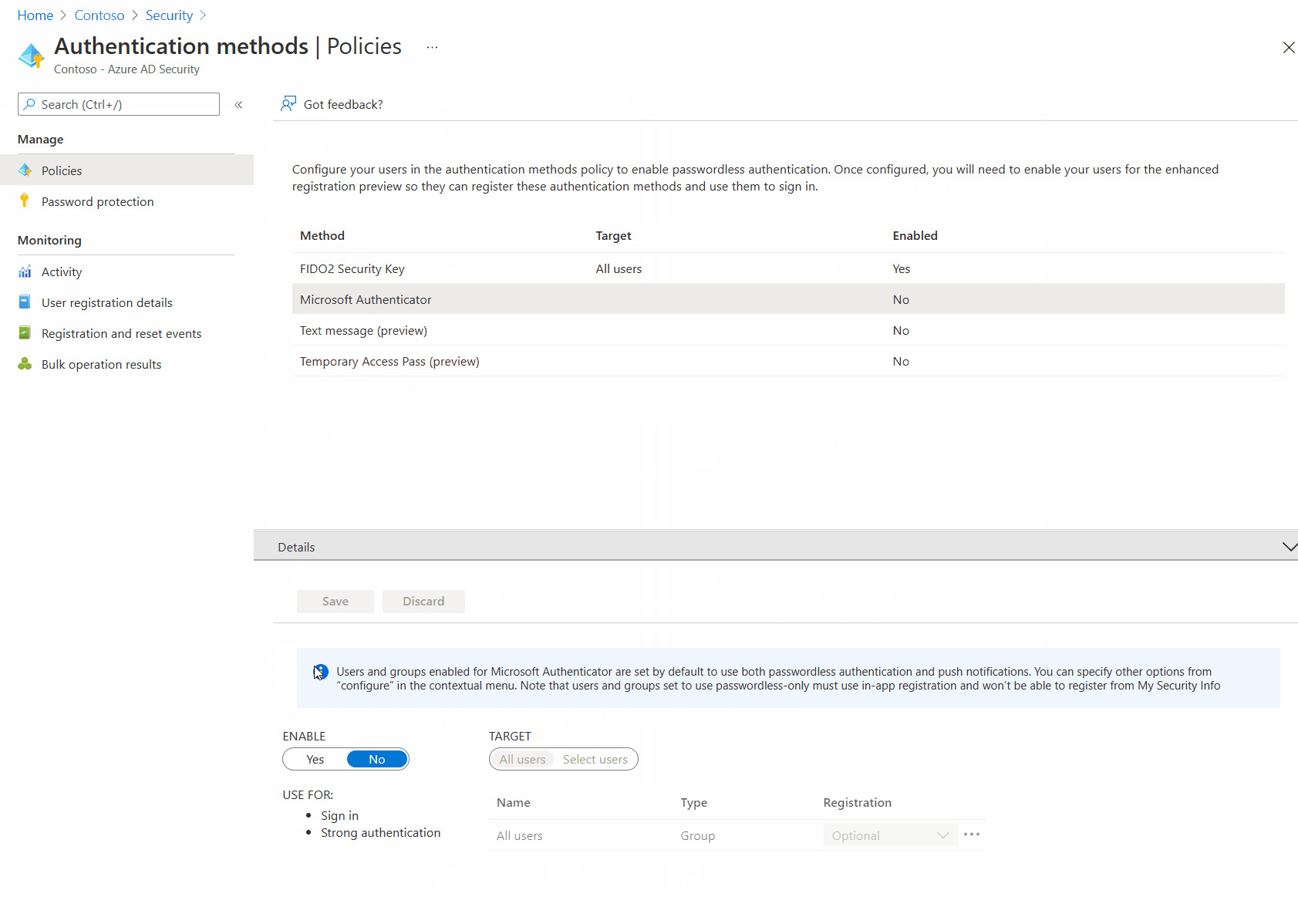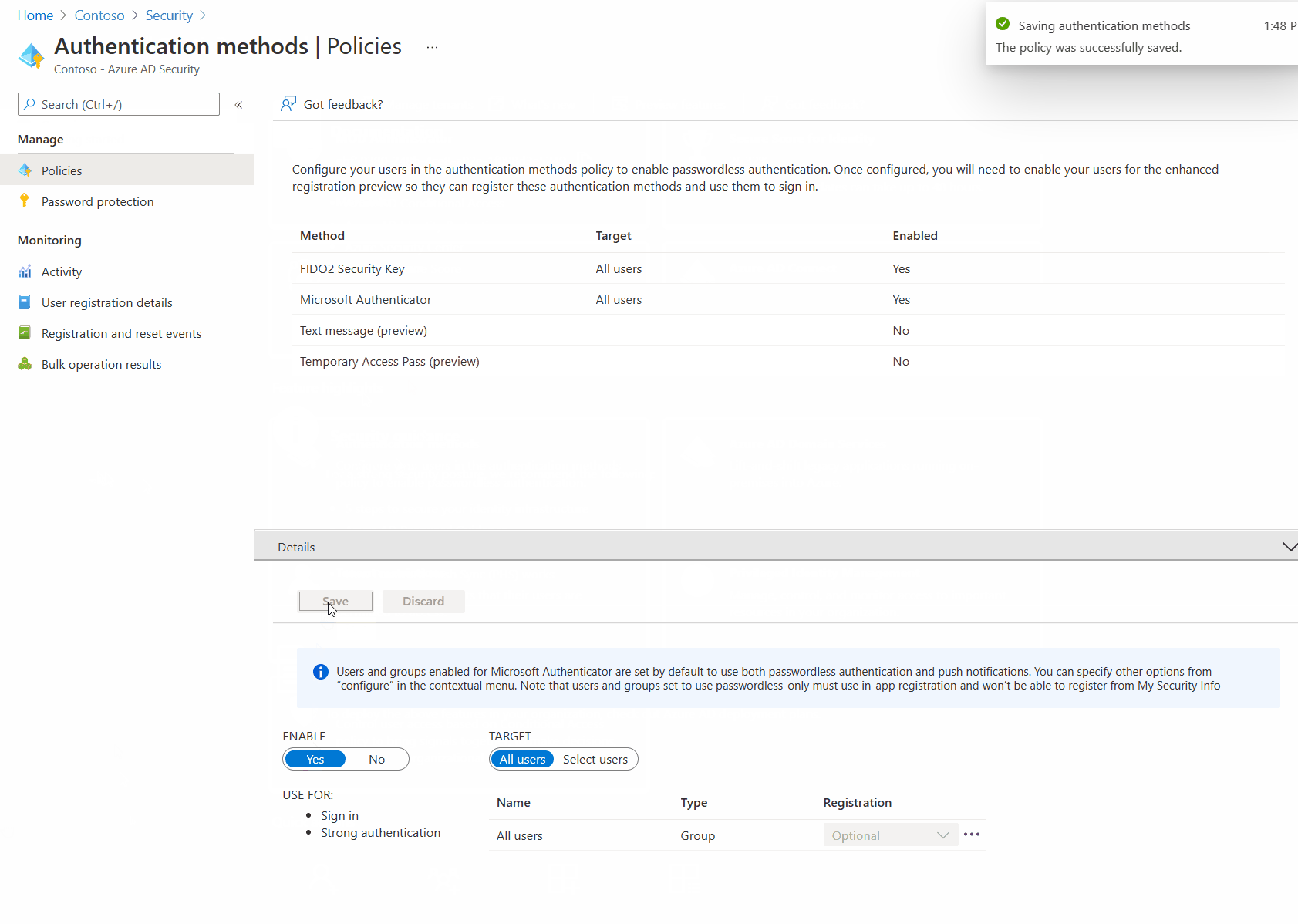
In order to use the Microsoft Authenticator passwordless option the authentication method must be enabled in Azure AD. Note that this authentication method does not prevent the use of the authenticator app regardless if the
- From the Azure AD blade select Security.
- Next select Authentication Methods.
- Select Microsoft Authenticator and click Enable.
- Save the settings.
Install Microsoft Authenticator
If you have already setup Microsoft Authenticator and you are already approving notifications for Multi-Factor Authentication then proceed directly to the Device Registration step.
- Open the Security Info page on the users profile.
- Click Add Method.
- Select Authenticator App from the dropdown list.
- Download the Microsoft Authenticator from the AppStore or Google Play
- Open the Microsoft Authenticator App and click the + sign to add a new account.
- Select Work or School account.
- Scan the QR code provided to automatically add the account.
- Microsoft will send the Microsoft Authenticator App a notification, approve the request.
- Microsoft Authenticator has now been added.
Device Registration
In order for Microsoft Authenticator to be used as a passwordless option, the mobile device needs to be registered to Azure AD. Device Registration is not the same as mobile device management (MDM) and does not provide the organization with any control or management capabilities on the mobile device. Device Registration simply associates a device to a specific user, since a device can only be registered to a single tenant we are limited to a single account that can be used for Passwordless Authentication with the Microsoft Authenticator app.
- Open Settings in the Microsoft Authenticator App.
- Select Device Registration
- Enter your email address and click Register Device
- Return to the main menu and select the account we added previously
- Select Enable Phone Sign-in.
- If the mobile device has been correctly registered to the organization, and a passcode/Touch ID/Face ID is set both checkmarks should appear. If any steps are missing the Authenticator app will attempt to resolve those issues prior to registering.
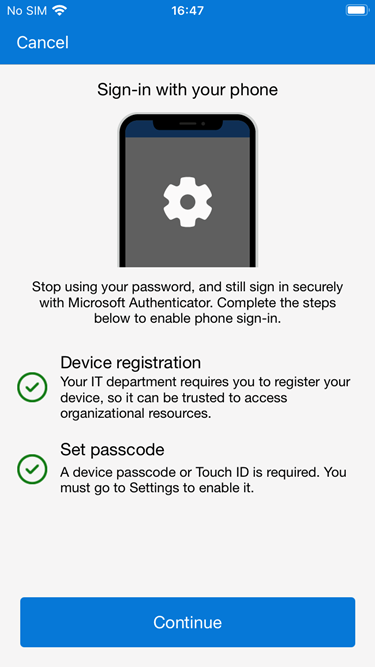
Our mobile device has now been configured for Passwordless Authentication through the Microsoft Authenticator App. We can now do a test to verify that everything works as expected.
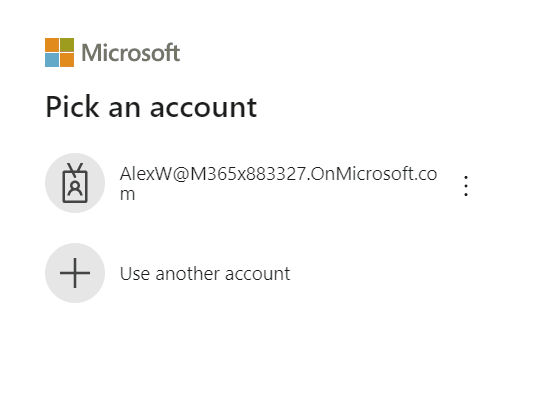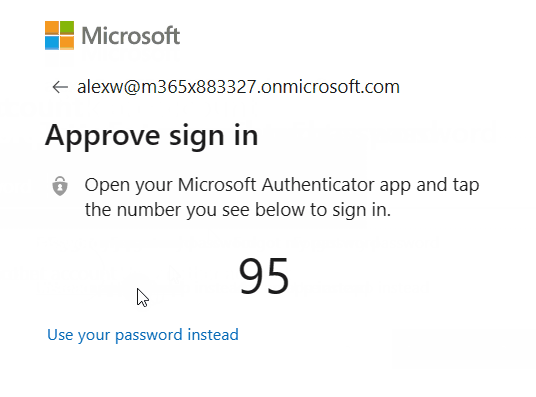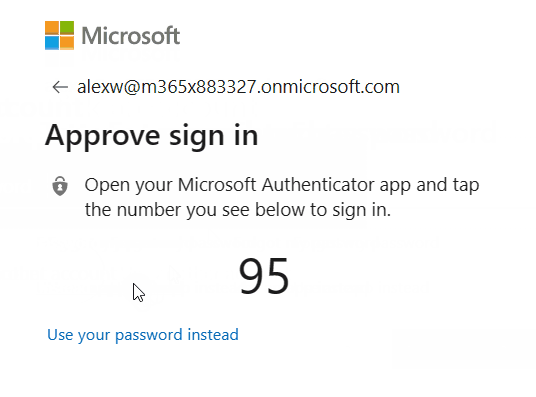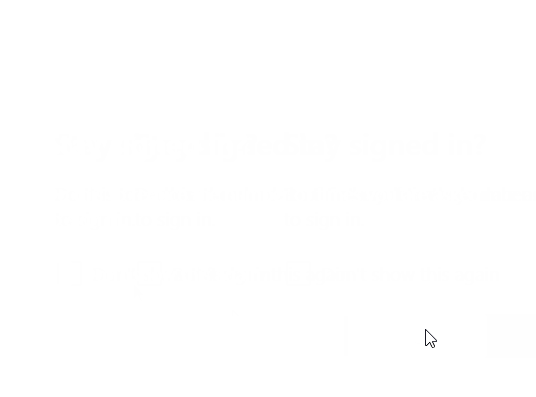
Sign-in Using Passwordless Authentication
- Open a new Incognito/In-private window on your PC browser.
- Browse to any Microsoft 365 service such as https://portal.office.com.
- Enter your Username (email address).
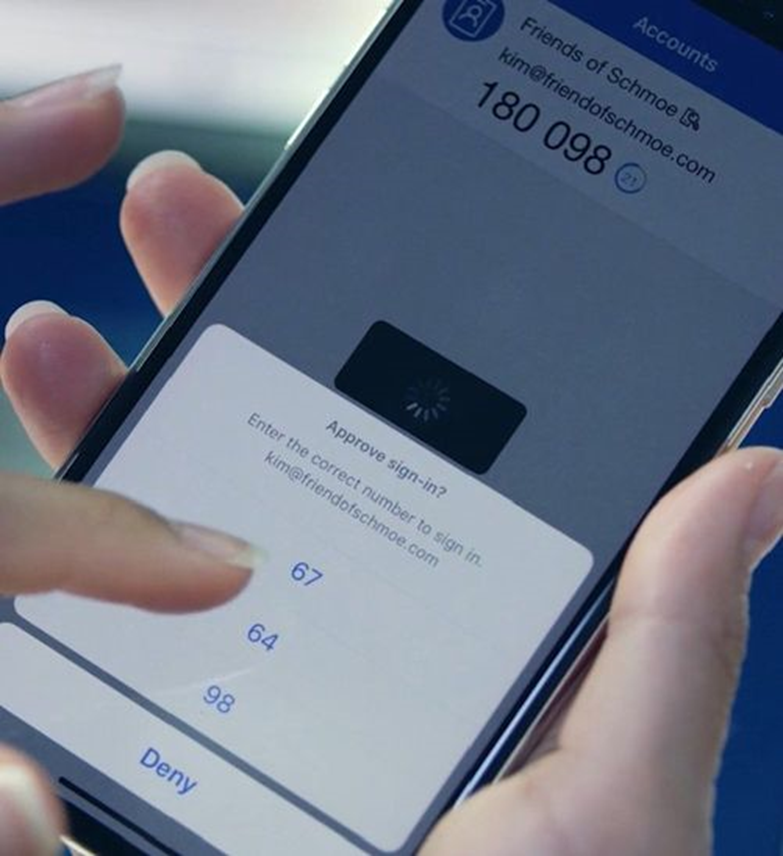
- If required select Use an App Instead.
- In the Microsoft Authenticator select the corresponding number that is displayed on the screen.
- You are now signed-in.