Ask yourself how many accounts do you have? Facebook, Twitter, Gmail, Microsoft Accounts, Online banking, Amazon and other shopping platforms, the list goes on and on. Of those accounts how many are using the same password? Probably many. On average a single person has roughly 100 different accounts but rarely 100 different passwords. Some argue that they have Multi-Factor Authentication (MFA) on all their accounts and hence they are protected. Yes MFA does increase security, but it is not the best user experience nor does it solve our dependency on passwords. In this post we will activate passwordless authentication using FIDO2 Security Keys in Azure AD, and demonstrate how we can access our Microsoft 365 services and sign-in to our Azure AD joined device without passwords.
Note that this is one of several methods to achieve Passwordless Authentication. See my post on Getting Started with Passwordless Authentication to understand why passwordless authentication is an important change for the future and explore other methods.
Passwordless login represents a massive shift in how billions of users, both business and consumer, will securely log in to their Windows 10 devices and authenticate to Azure Active Directory-based applications and services.
Alex Simons, Corporate Vice President PM, Microsoft Identity Division
Contents
- What are FIDO2 Security Keys
- Requirements
- Enable Combined Security Information Registration
- Enable FIDO2 in Azure AD
- Registering a FIDO2 Security Key
- Using a Security Key with Microsoft 365
What are FIDO2 Security Keys?
A large group of companies that together form the FIDO Alliance (Fast Identity Online), have the last few years been working to solve the worlds dependency on passwords. They are focusing on USB based security keys, badges and other wearables that allow us to authenticate by using something we are (biometrics) or something that we have (device/badge/USB Key etc..) rather than something we know (password/secret).
Up to 51% of passwords are reused
There are many types of FIDO2 Security Keys out there, but my recommendation would be to get one that supports biometrics. With biometric support the key can be unlocked with for example a fingerprint instead of a PIN that is knowledge based. It should be stated that not all FIDO2 implementations require a PIN code to unlock a FIDO2 device without biometrics like Microsoft does. Having a security key that needs to be unlocked with a PIN code is great for testing but is not what you want in production in my opinion (with an exception for shared devices). Although a PIN is better than a password since the PIN is specifically bound to a particular device, our end goal should be moving away from knowledge based factors.
Requirements
- Azure AD Multi-Factor Authentication enabled and configured.
- Enabled Combined Security Information Registration (automatically enabled for newer tenants).
- Compatible FIDO2 security key.
- Windows 10 1903 or later (Windows 10 2004 or later for Hybrid Joined devices).
Enable Combined Security Information Registration
The first step is to make sure that Combined Security Information Registration is enabled in the Microsoft 365 tenant. By enabling this feature users do not have to register their security information multiple times for multiple services. For example the security information that a user provides for Multi-Factor Authentication (MFA) can be automatically used for Self-Service Password Reset (SSPR).
- From the Azure AD blade select User Settings.
- At the bottom select Manage User Feature Settings.
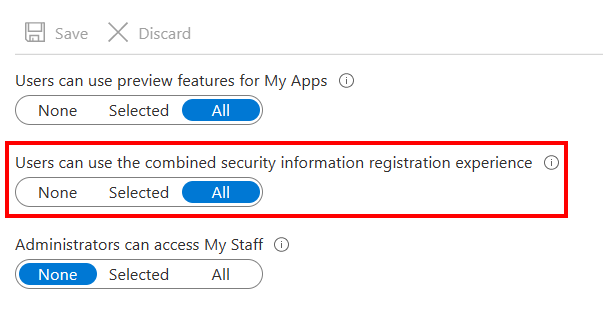
- Make sure that the Users can use the combined security information registration experience is set to All as in the picture below.
Enable FIDO2 Authentication in Azure AD
Now that the Combined Security Information Registration feature is enabled we can enable FIDO2 Security Keys as an Authentication Method in Azure AD.
- From the Azure AD blade select Security.
- Next select Authentication Methods.
- Select FIDO2 Security Key and click Enable.
- Save the settings.
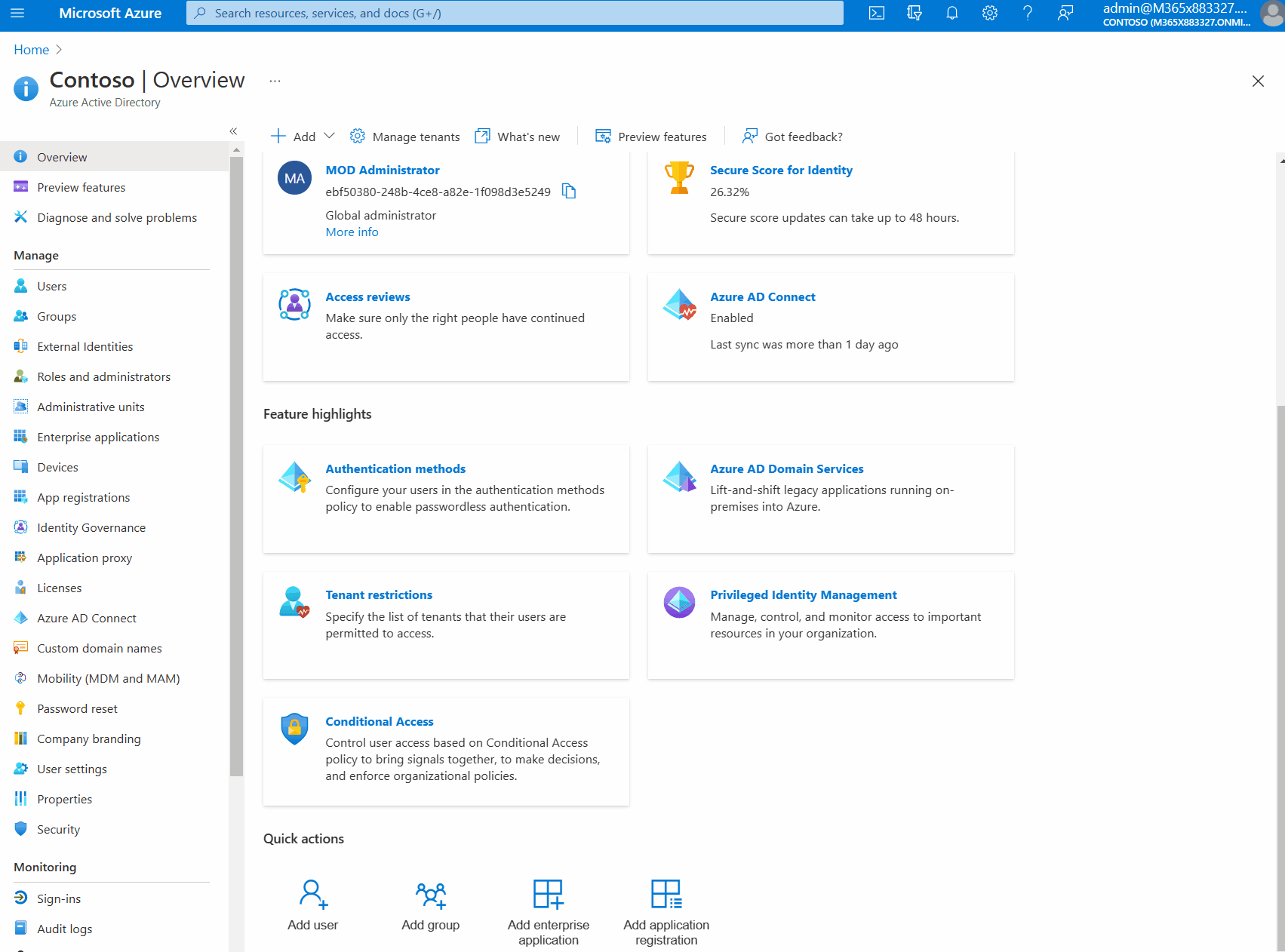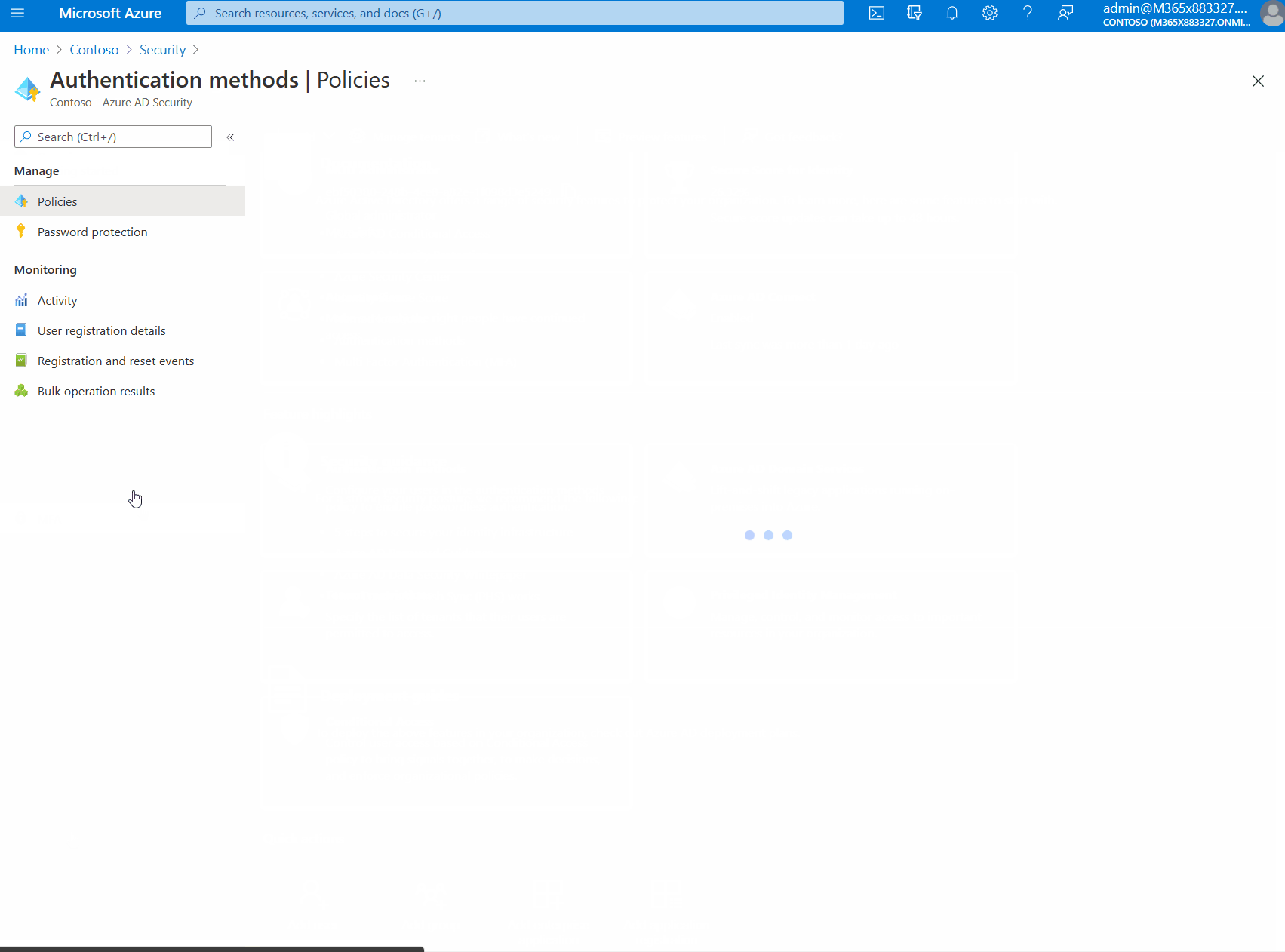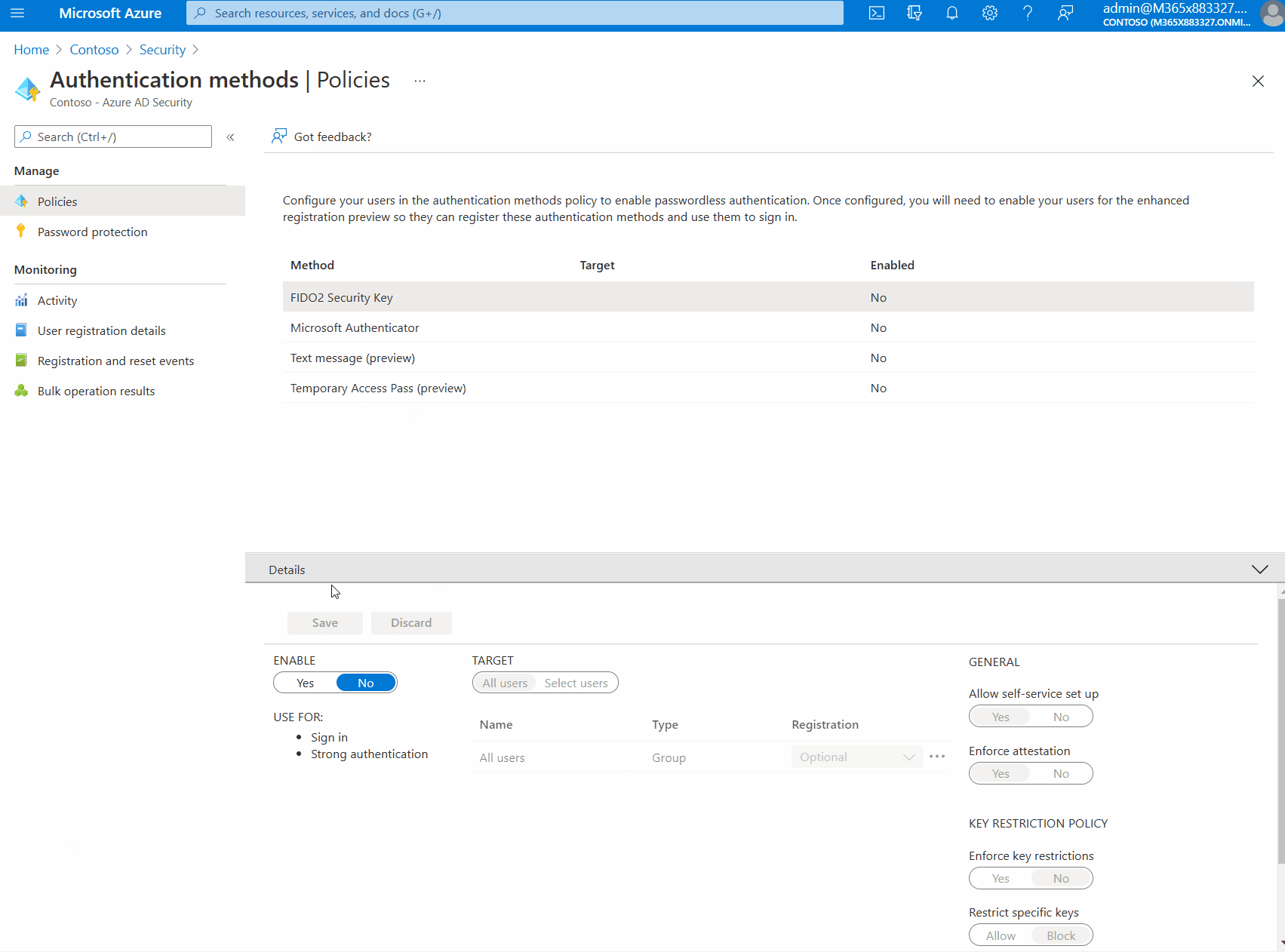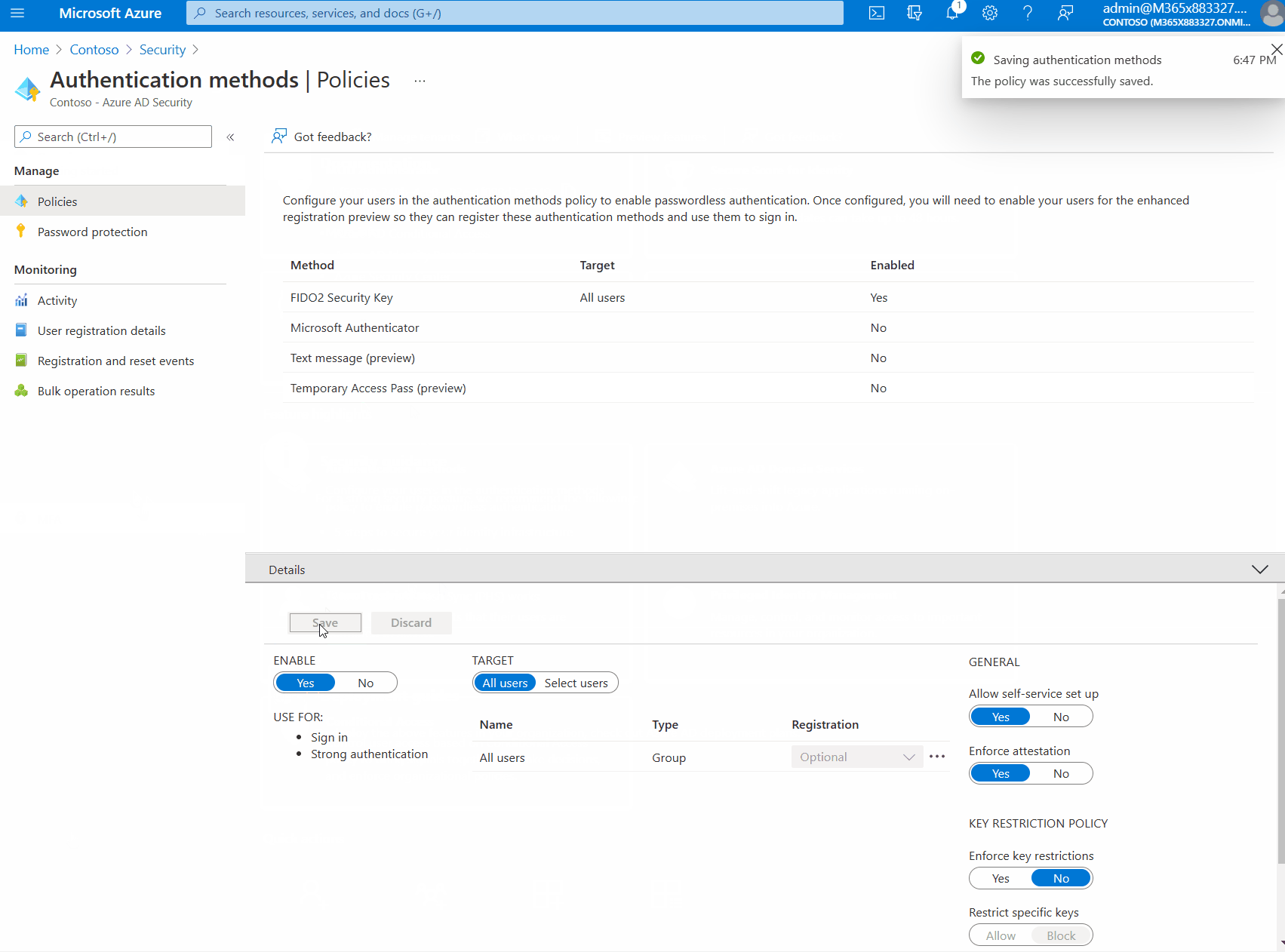
When enabling FIDO2 Security Keys a few optional settings are displayed:
Allow Self Service Setup: When set to No users are not able to register new FIDO2 keys even if the Authentication Method is enabled.
Enforce Attestation: Requires the FIDO security key metadata to be published and verified with the FIDO Alliance Metadata Service. Microsoft requires some specific features from the FIDO2 CTAP protocol before the device is considered Microsoft compatible. If your device does not meet these criteria you might have to disable Attestation in order to register they key.
Restrict Specific Keys: Allows organizations to allow or disallow specific FIDO2 Security Keys. Keys are identified using the Authenticator Attestation GUID (AAGUID) as specified in the FIDO2 Specification.
Register a FIDO2 Security Key
To register a FIDO2 security key users will need to be enrolled into Multi-Factor Authentication before a FIDO2 security key can be added. In the bellow example a YubiKey 5 was used, the process could be slightly different depending on the make, model and features of your security key.
Tip: Since Strong Authentication is required in order to register a FIDO2 Security Key, consider using Temporary Access Pass for new users that might not have MFA already configured. This would allow new users to register a FIDO2 Security Key without going through MFA registration first. On future sign-in the user would then authenticate with their FIDO2 based device.
- Open the Security Info page on the users profile.
- Click Add Method.
- Select Security Key from the dropdown list .
- Choose if your security key is USB or NFC based (select USB for Bluetooth).
- A popup will appear, verify that the correct user is specified and press OK to continue.
- Press OK on the second popup to allow creating a credential on the security key.
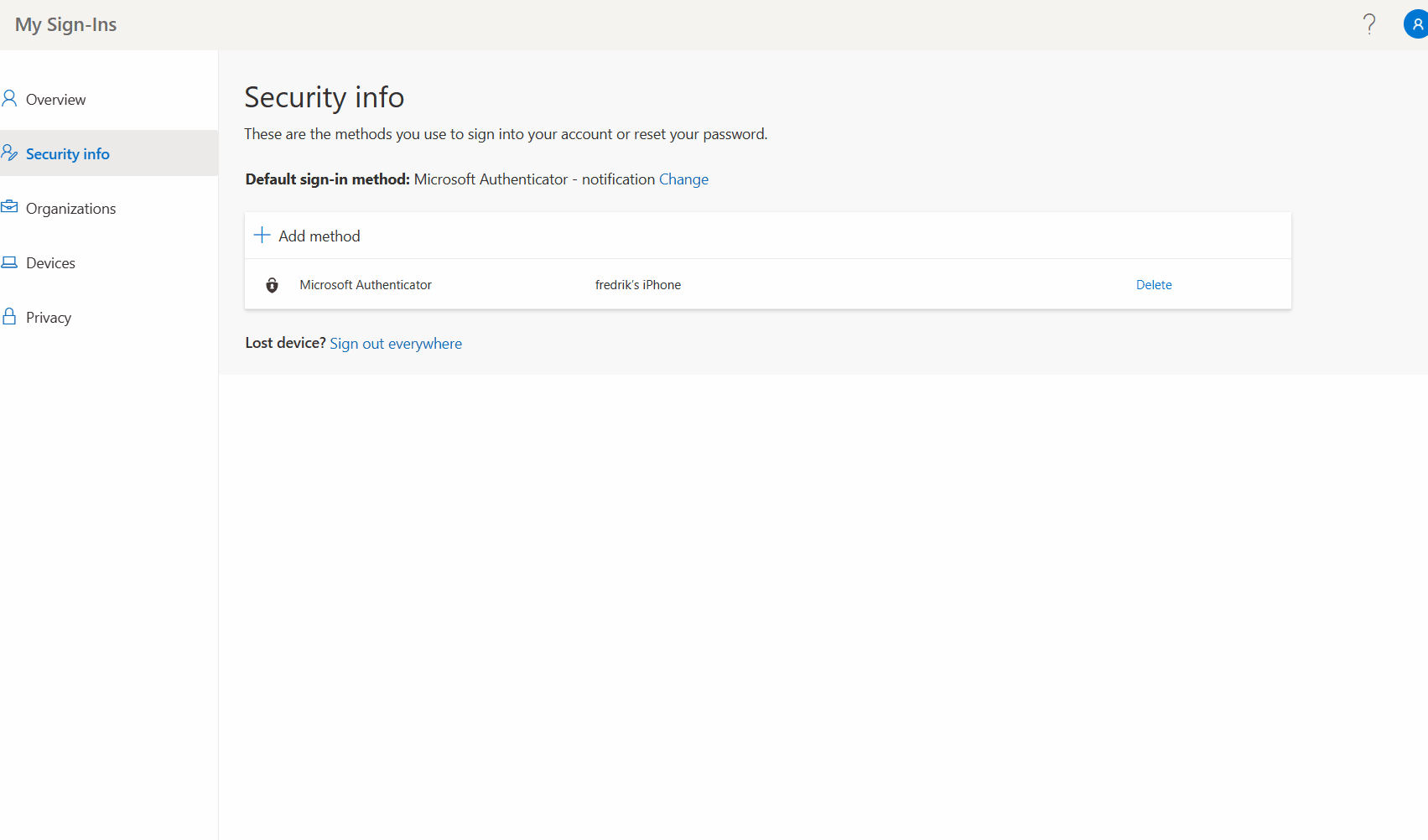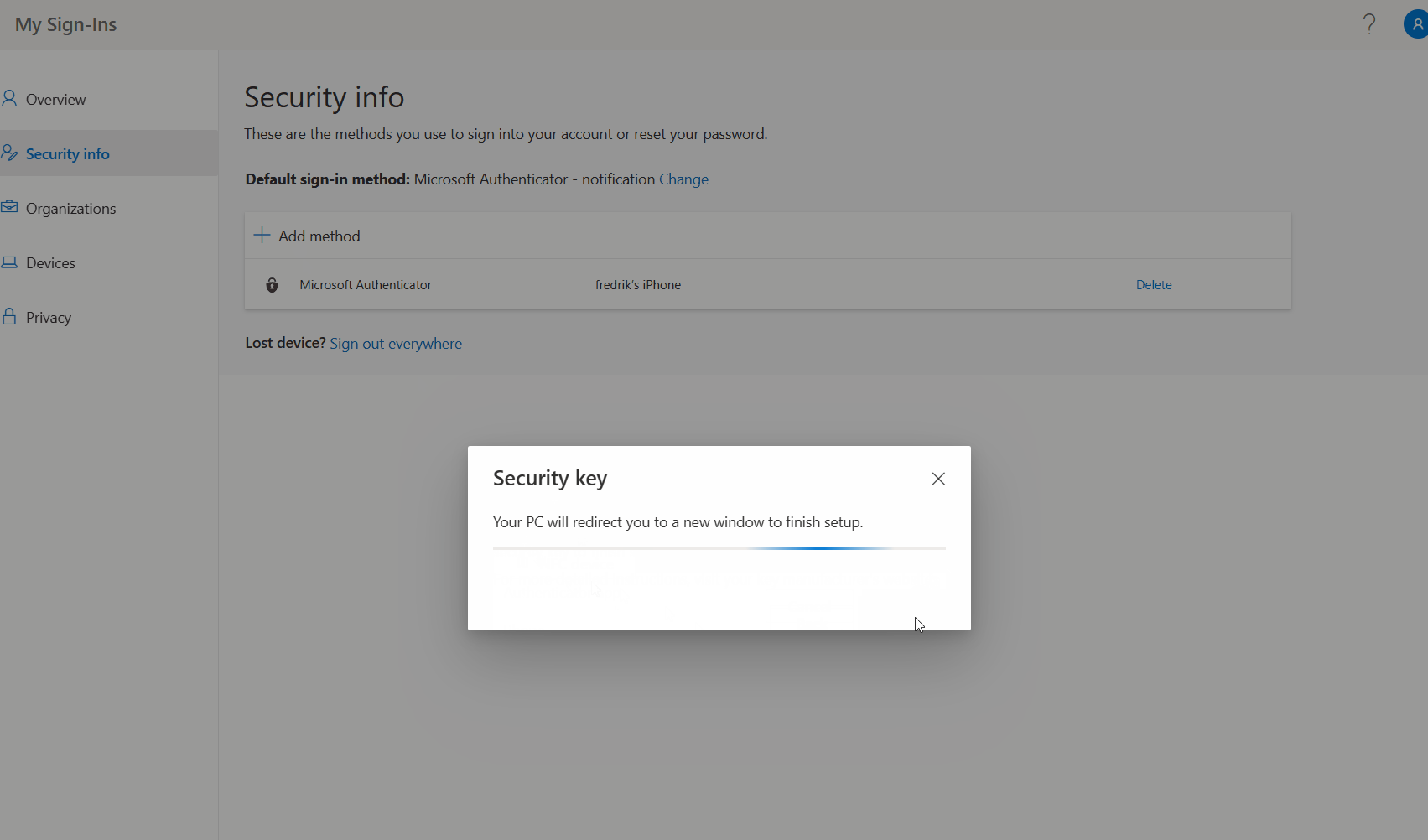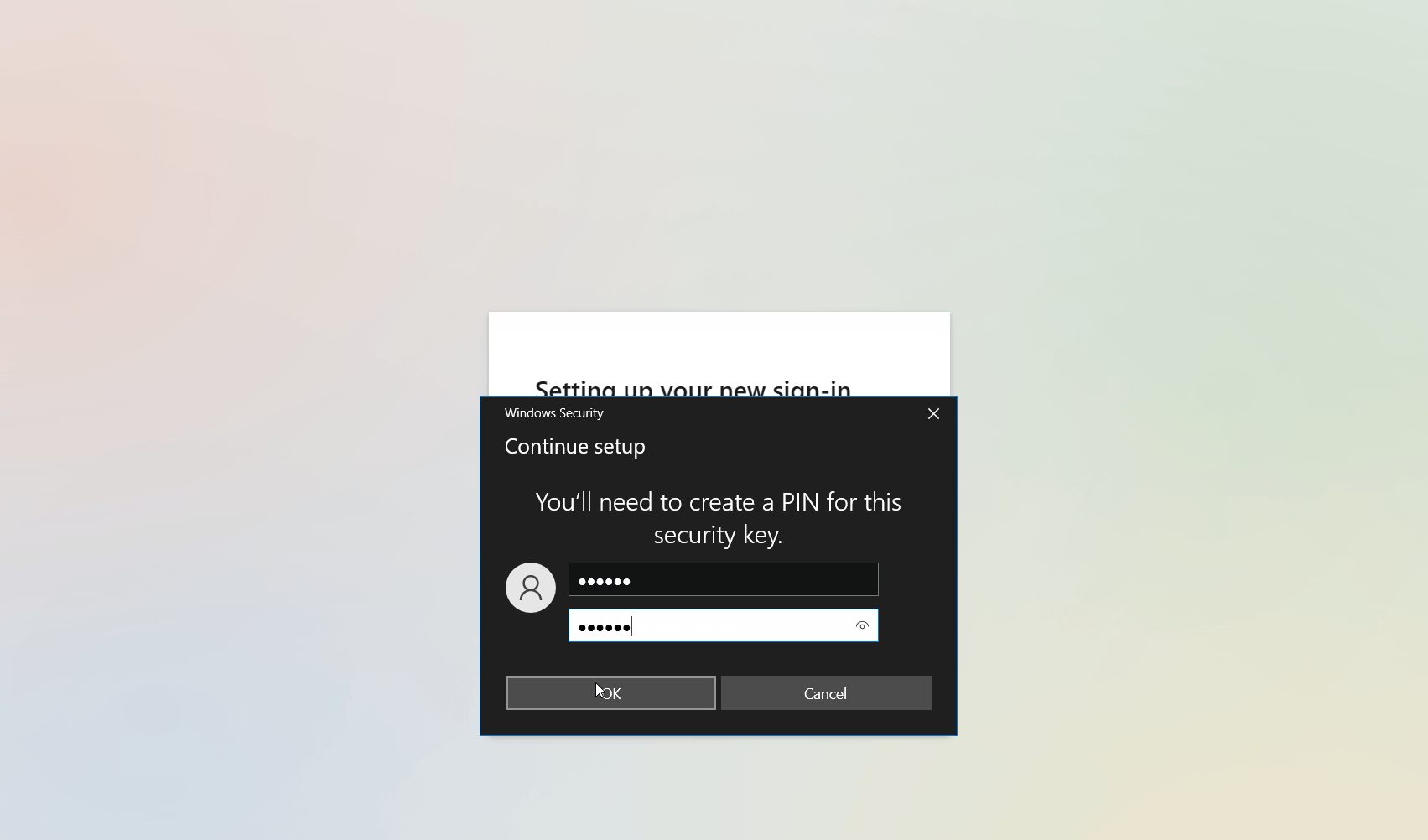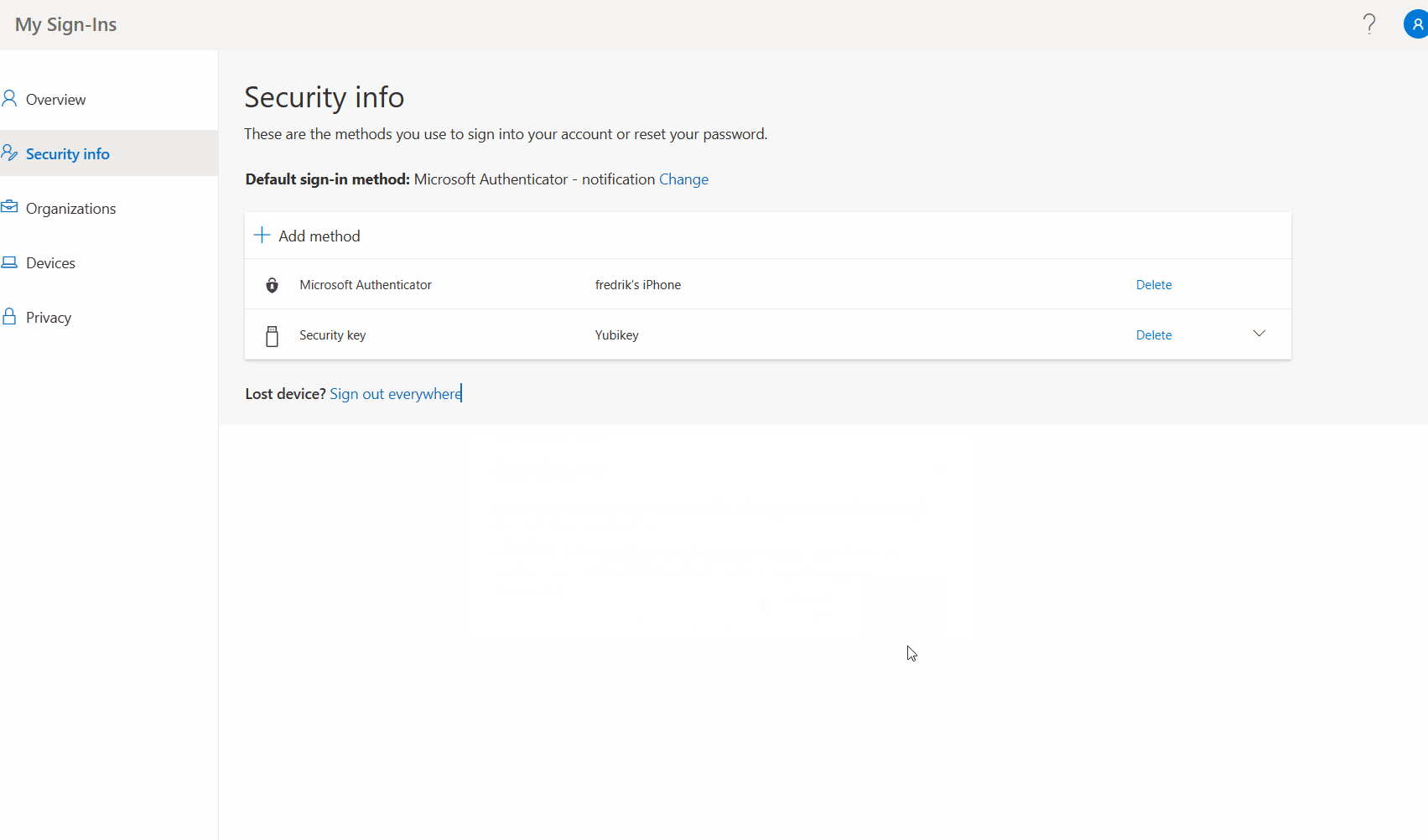
- Create a PIN that will be used to access the security key.
- Touch the security key to store the PIN.
- Give your security key a name.
Note: You might receive an error if the FIDO2 Security Key does not cover all of Microsoft’s requirements. In this case disable the Enforce Attestation setting in the FIDO2 Security Key Authentication Method.
Use a Security Key With Microsoft 365
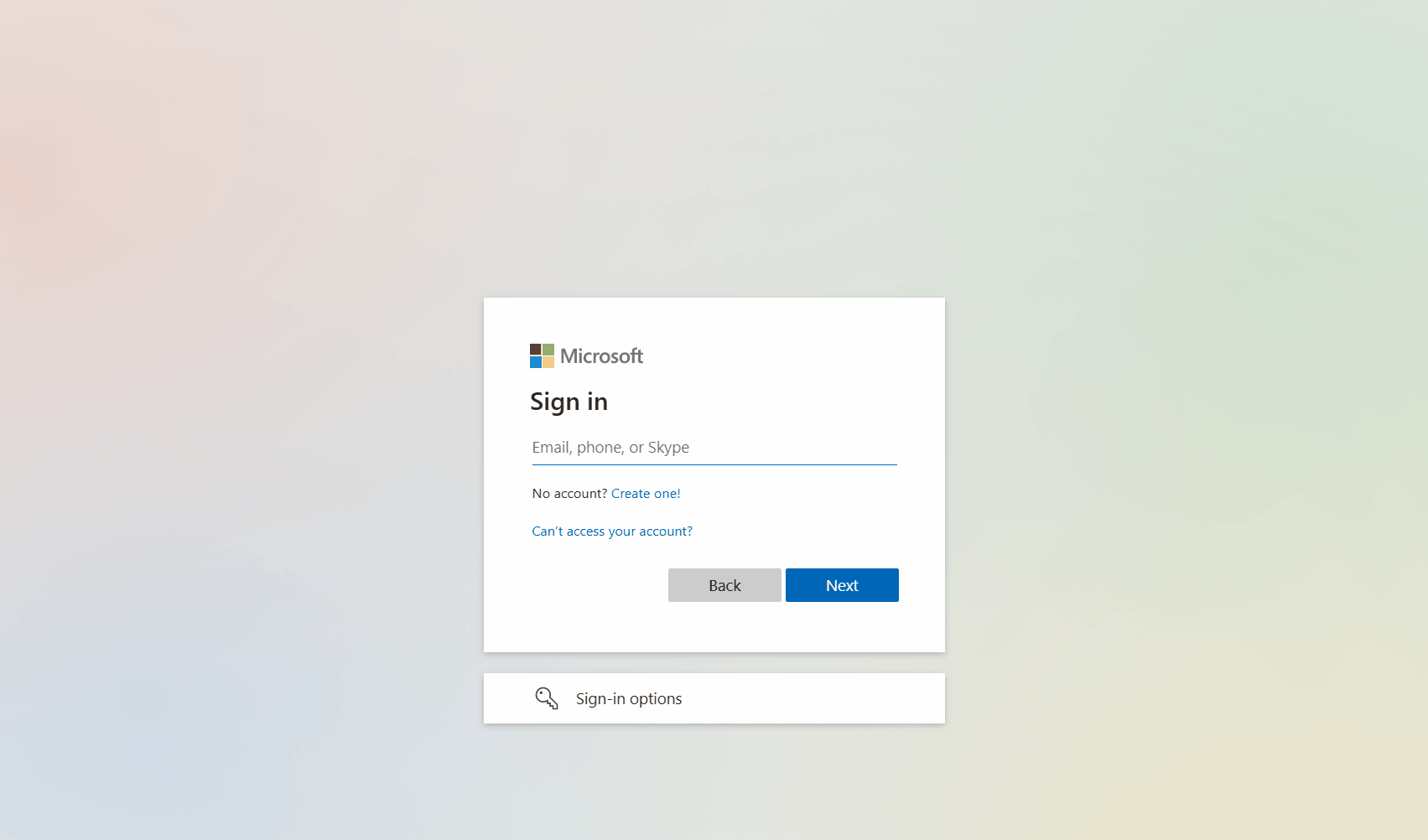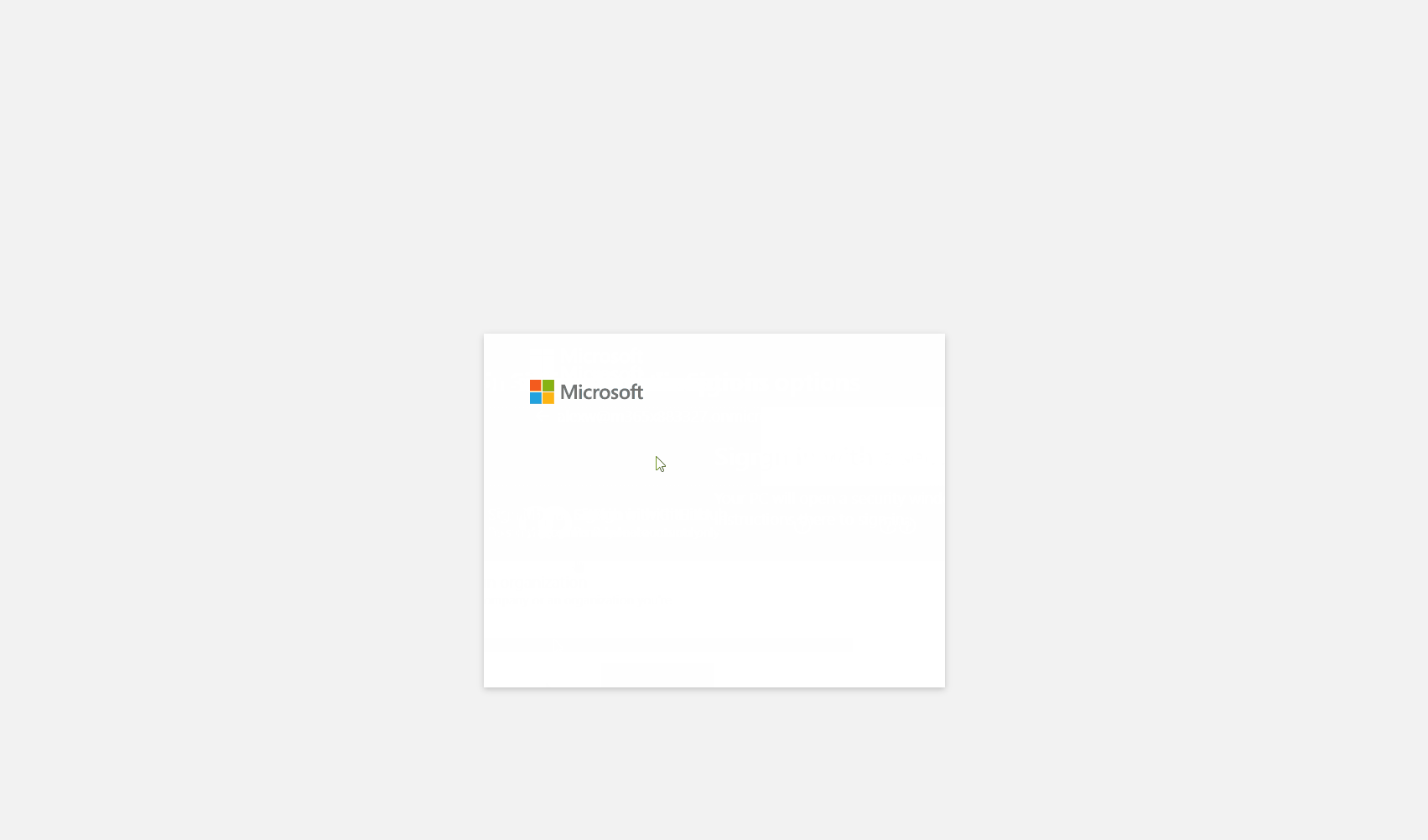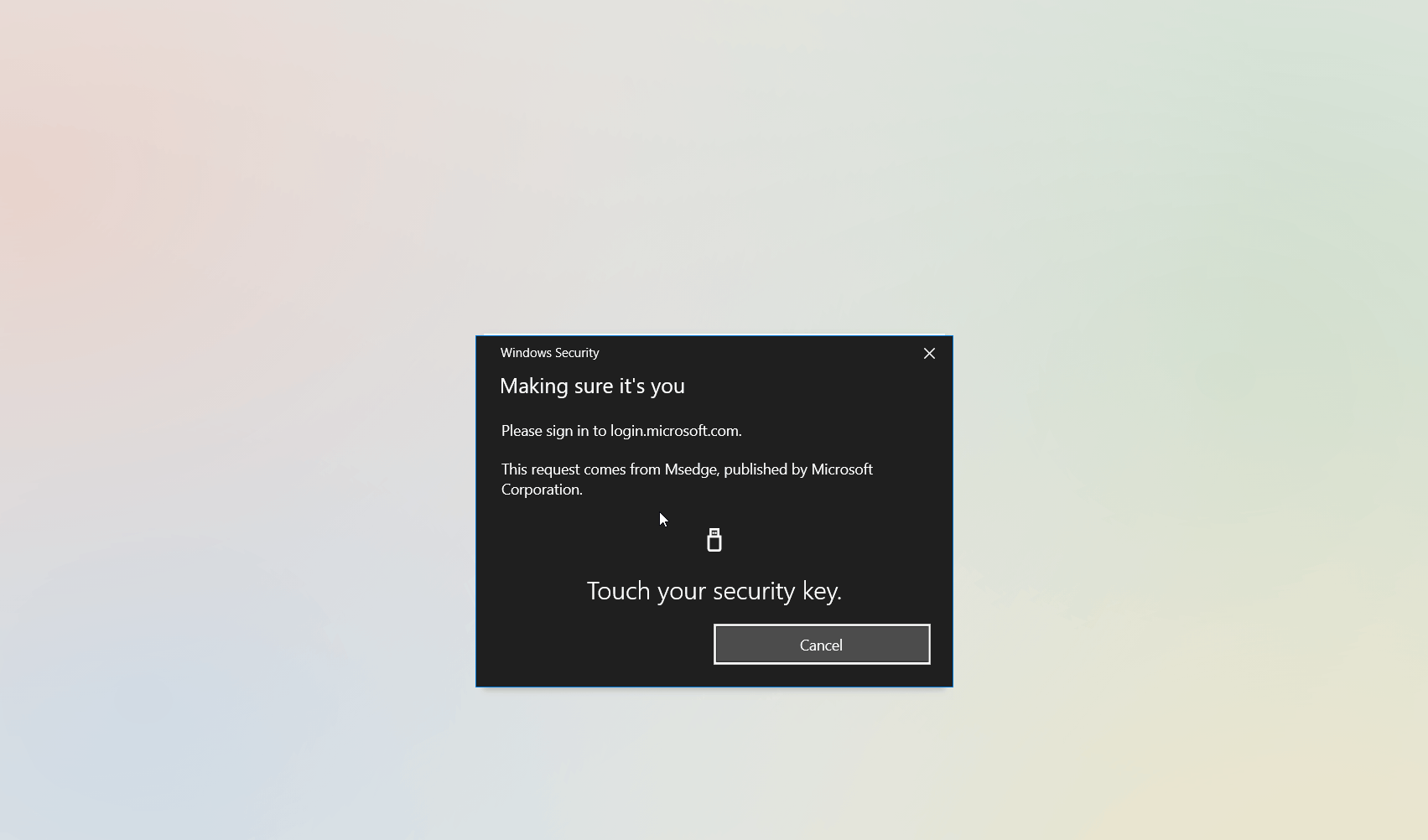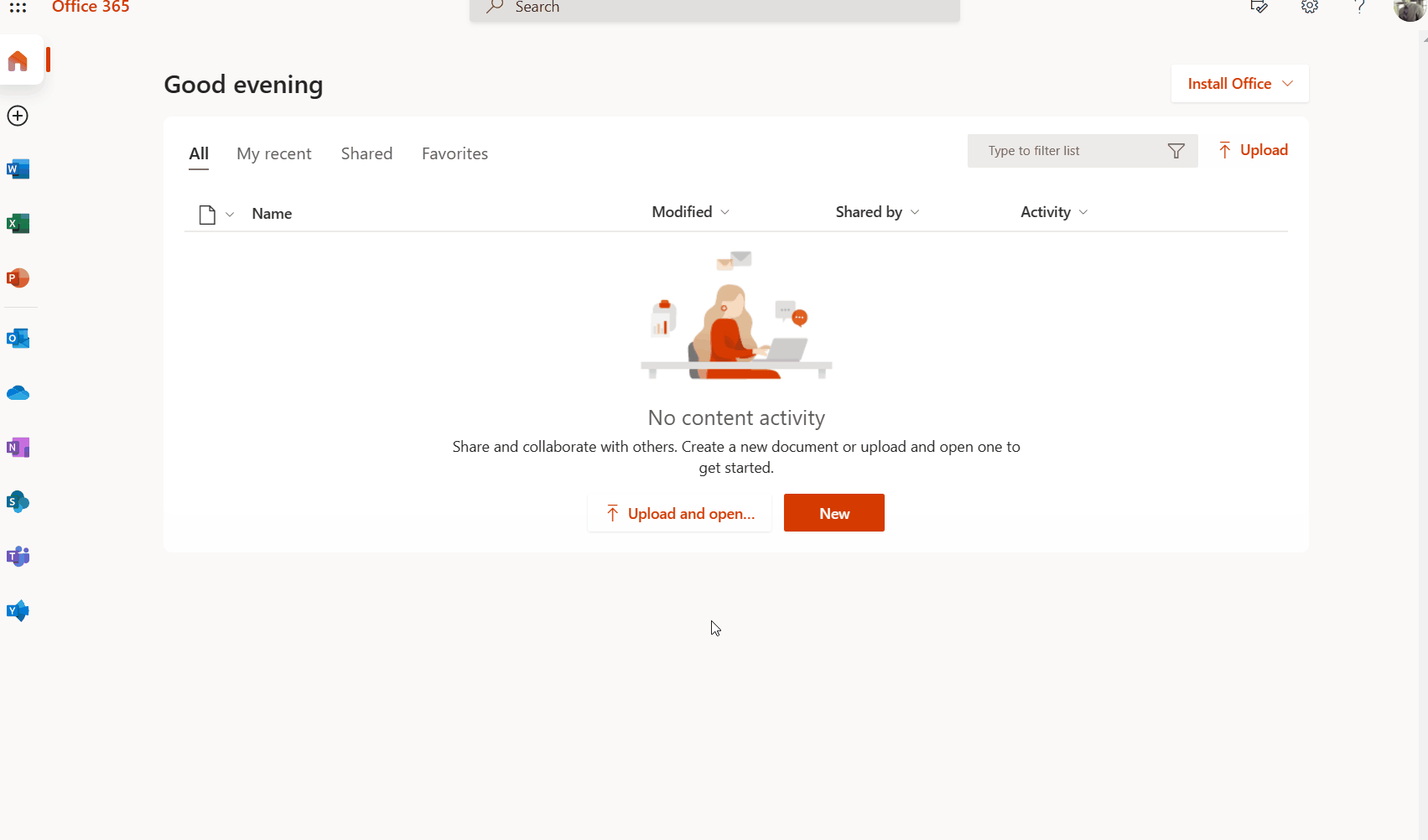
In the below example a test user attempts to logon to Microsoft 365 Portal using the same security key that was registered in the previous step. The same procedure would work for other Microsoft 365 services such as Outlook, SharePoint or Teams.
A user navigates their supported browser to a Microsoft 365 application, in this case the Office 365 Portal. Instead of specifying their username and password, the user chooses Sign-in Options and selects the Security Key option. The user is then asked to specify the PIN code for their security key and is signed-in to the application.