Imagine being able to come to the office and do your job without needing to enter a single password. It might seem like something from the future, the reality is that this technology is available today and many applications and services already support it.
Many people confuse Passwordless Authentication with Multi-Factor Authentication (MFA). MFA adds an extra layer of security in addition to a password such as a code from an app or SMS. Passwordless Authentication refers to the ability of being able to access a system or service, without specifying a password or secret that is knowledge based. This not only increases security but also provides end-users with a much better experience (not to mention the reduction in support calls dealing with forgotten passwords). In this post we will discuss some of the problems with traditional passwords, why and how businesses/individuals can start their passwordless journeys, and explore some of the passwordless methods available in Microsoft environments (regardless if you are on-premise, hybrid or in the cloud).
By 2022, Gartner predicts that 60% of large and global enterprises, and 90% of midsize enterprises, will implement passwordless methods in more than 50% of use cases.
Contents
- The Problem With Passwords
- Starting a Passwordless Journey
- FIDO2 Security Keys
- Microsoft Authenticator
- Windows Hello for Business / Convenience

The Problem With Passwords
A password is a secret word or phrase that should only be known to the user and the service/application (identity provider). To improve security most corporations implement a password policy that requires complex passwords consisting of uppercase, lowercase, numbers and special characters with a specific length requirement. Additionally many corporations have time constraints on how long a password is valid before it has to be changed. Unfortunately passwords are becoming more and more ineffective to modern attacks like phishing, password spray or brute-force to mention a few. Another factor that attackers exploit is the human aspect. Since we are all humans, and coming up with unique and complex password is hard for humans, not to mention memorizing them. 91% of us know that using the same or variation of the same password is a risk, however 66% percent do it anyway according to the Psychology of Passwords study done by LastPass in 2020.
81% of hacking-related breaches leveraged either stolen and/or weak passwords.
Verizon
So should we just get rid of passwords altogether? In an ideal world the answer would be yes, however in reality passwords will most likely be with us for the foreseeable future. The reason is simple, password authentication works with just about everything regardless if it is an application, document, service or device. Completely getting rid of password authentication in a single organization would not only take a considerable amount of time, but also require development and investments as many companies have systems that might not support other authentication methods. Nevertheless, all companies should start investing and planning for a world without passwords as passwordless authentication should be the long term goal. There are many services and systems that already support passwordless options, so get started today it is easier than you might think!
52% of users haven’t changed their password even after hearing about a breach in the news.
LastPass
Since passwords are easily exposed to phishing, password sprays, brute-force etc.. the most important thing administrators can do in the short-term, is to implement Multi-Factor Authentication on all their systems. Even if a password is exposed through a data breach, an attacker would still need a second factor to access the exposed account. According to Microsoft simply enabling MFA (Multi-Factor Authentication) reduces risk by 99.9%. Reducing our passwords usage would reduce the risk even further.
Multi-Factor Authentication works by combining a variety of factors. There are products that support additional factors such as location and adaptive authentication (risk based/behavior) but the most common methods are the three below:
- Something you know (secret/password/PIN)
- Something you have (device/key)
- Something you are (biometrics)
Our end goal should be Passwordless MFA, meaning that the authentication flow is passwordless but also uses multiple factors. Obviously the solution should only consist of factors that are either a) something you have or b) something you are. The result would bring high security but also a better end-user experience.
While we are on the subject of MFA, organizations should refrain from using phone call and SMS as a second factors. Don’t get me wrong any type of MFA is better than nothing, but phone and SMS are probably the least secure methods available today. Consider solutions like biometrics, hardware token or an app like the Microsoft Authenticator that are much more secure. Organizations and employees should also be encouraged to start using password managers. Having a long, complex, unique and random generated password per account reduces risk, as only a single account would be compromised in the event of a data breach.
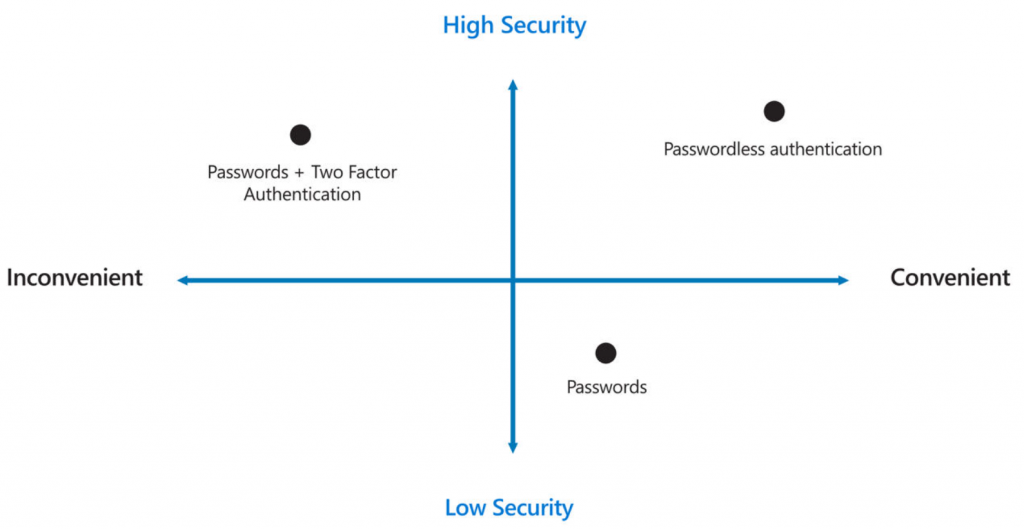
Starting a Passwordless Journey
Start a passwordless journey by making passwordless sign-in available on those systems/services that support it today. For those organizations utilizing Microsoft 365 and Azure AD, enable optional authentication methods such as FIDO2, Microsoft Authenticator and Temporary Access Pass in Azure AD. Modernize client hardware, Windows 10/11 devices can leverage Windows Hello for biometric sign-in such as fingerprint or facial scan. In order to take advantage of biometric sign-ins and modern security features, a device with a TPM 2.0 and biometric hardware is required (will be required for Windows 11). FIDO2 Security Keys provide a great alternative if the hardware in your organization does not support biometric logons, or if you have shared devices. Finally disable the use of Legacy Authentication protocols, this means any protocol that does not support multi-factor authentication. Since passwordless authentication is a long term goal the most important thing is to reduce our dependency on passwords over time. This means making a strategy that makes sure new investments in software and services support both modern authentication and passwordless authentication.
Passwordless login represents a massive shift in how billions of users, both business and consumer, will securely log in to their Windows 10 devices and authenticate to Azure Active Directory-based applications and services.
Microsoft
Recommendations:
- Start a passwordless journey today!
- Enable Passwordless Authentications methods for systems that support it.
- Your password does not really matter anymore (even if it is 50 characters).
- Disable Legacy Authentication.
- Enable Multi-Factor Authentication for all systems.
- Modernize Hardware with TPM 2.0 and Biometric support.
- Single random password per account.
- Require password change only if user is compromised
- Use password managers for both private and corporate accounts.
- Re-evaluate password policies.
- Passwords will be with us for the foreseeable future but start reducing the dependency on them.
- When investing in new system/applications make sure they support passwordless authentication.
FIDO2 Security Keys
FIDO or Fast Identity Online is an alliance of companies that have come together to solve the worlds dependency on passwords. They have come up with the FIDO2 specification that allows us to login to our systems without passwords (uses private/public keys). FIDO2 Security Keys come in all shapes and sizes. They can be small USB devices but also badges, cards or other wearables like the examples from Yubico and FEITIAN Technologies below.
As devices like these become more and more mainstream, we will be able to securely access our devices and services by just tapping our employee badge to authenticate.
Looking to implement or learn more? See my post on FIDO2 Security Keys with Azure AD or FIDO2 Security Keys in Windows (Coming Soon).
Microsoft Authenticator
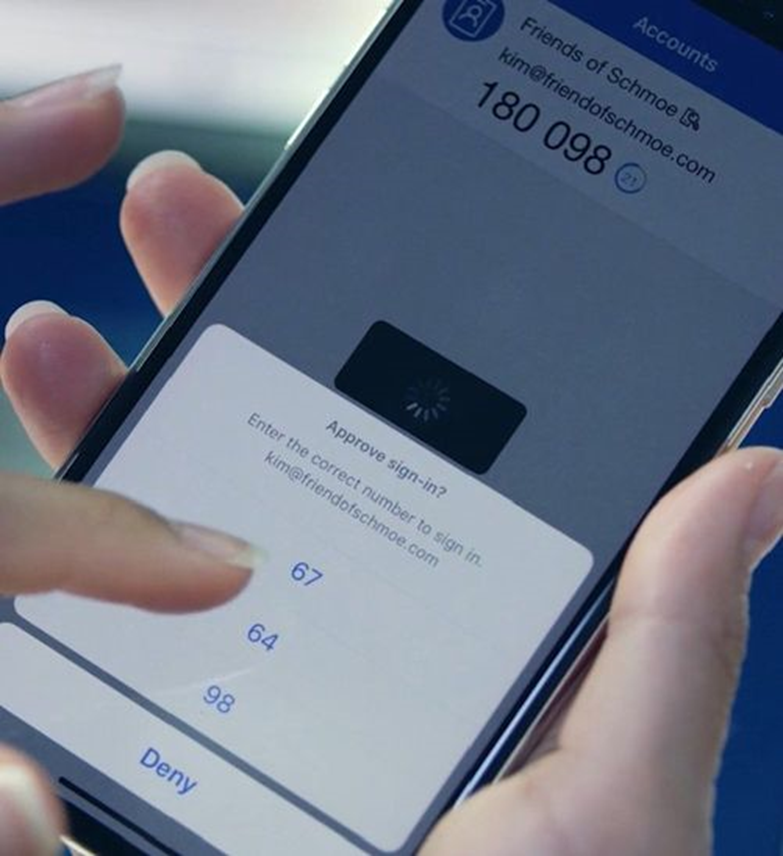
Microsoft Authenticator is an app for your smart phone or tablet that you might be using today for Multi-Factor Authentication. However the Microsoft Authenticator app can also be used for passwordless authentication (but limited to a single account). When the Microsoft Authenticator is used for passwordless authentication, a random number is displayed during the authentication process. The user then simply selects the corresponding number displayed in the Authenticator app, and the user is authenticated.
Looking to implement or learn more? See my post on Passwordless Authentication with Microsoft Authenticator.
Windows Hello for Business/Convenience
Windows Hello is a feature built into Windows 10/11 that allows a user to sign-in using either a PIN or biometrics such as facial or fingerprint recognition. There are actually two variants of the product, the first is called Windows Hello and is intended for private use as a more convenient way of signing into a device. Windows Hello for Convenience as we will call it going forward, still uses password based authentication but without the user having to enter the password, hence convenience. The second variant called Windows Hello for Business is drastically more secure because unlike Windows Hello for Convenience, it is backed by asymmetric private/public key pairs or certificate based authentication.
Unlike passwords or secrets a Windows Hello credential is never sent over the network for verification, meaning it is tied to a specific device. The same principle applies to Windows Hello PINs. A question that often comes up when customers are testing Windows Hello is: How can a PIN be more secure than a password? Most people associate the word PIN with a , but a PIN can also consist of alpha-numeric characters.
Looking to implement or learn more? See my post on Getting Started with Windows Hello (Coming Soon).